Understanding Azure Built-in Roles’ Impact on User Authentication Methods Blade
I recently encountered an interesting issue while attempting to manage authentication methods for different users. In this blog post, I will share the journey of my investigation, the discoveries, and the ultimate conclusion I reached.
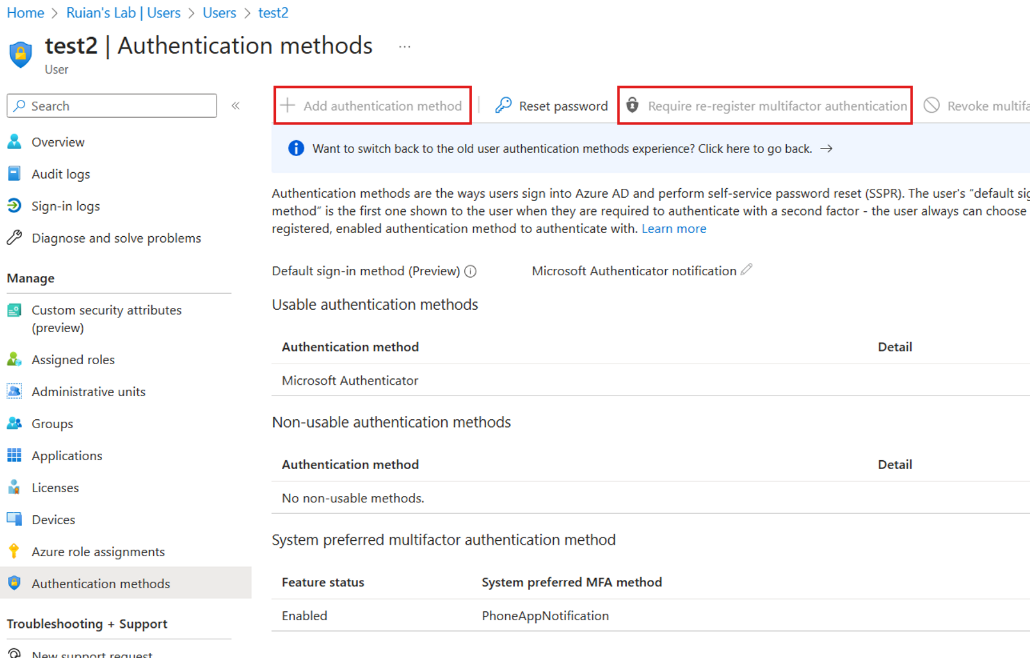
Issue Description
User has been assigned the necessary role to manage user authentication methods, including resetting Microsoft MFA (Multi-Factor Authentication) and creating Temporary Access Passes (TAPs) for certain end-users.
However, during our attempts to perform these operations, I encountered two distinct behaviors. Some users allowed me to carry out the required actions, while others presented these options as greyed out, preventing us from proceeding further.

Issue Analysis
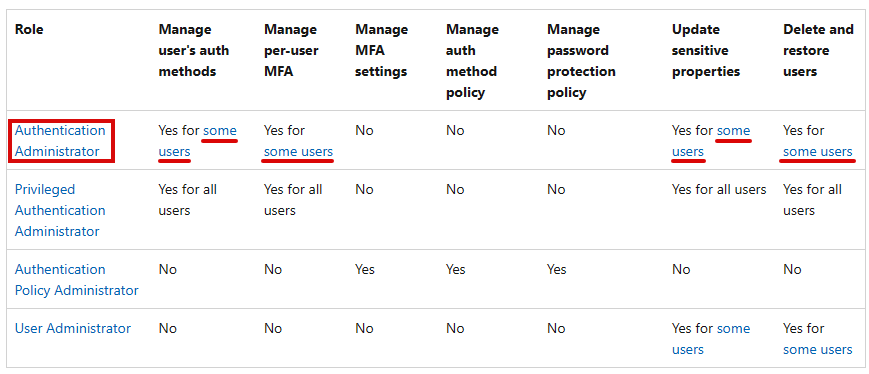
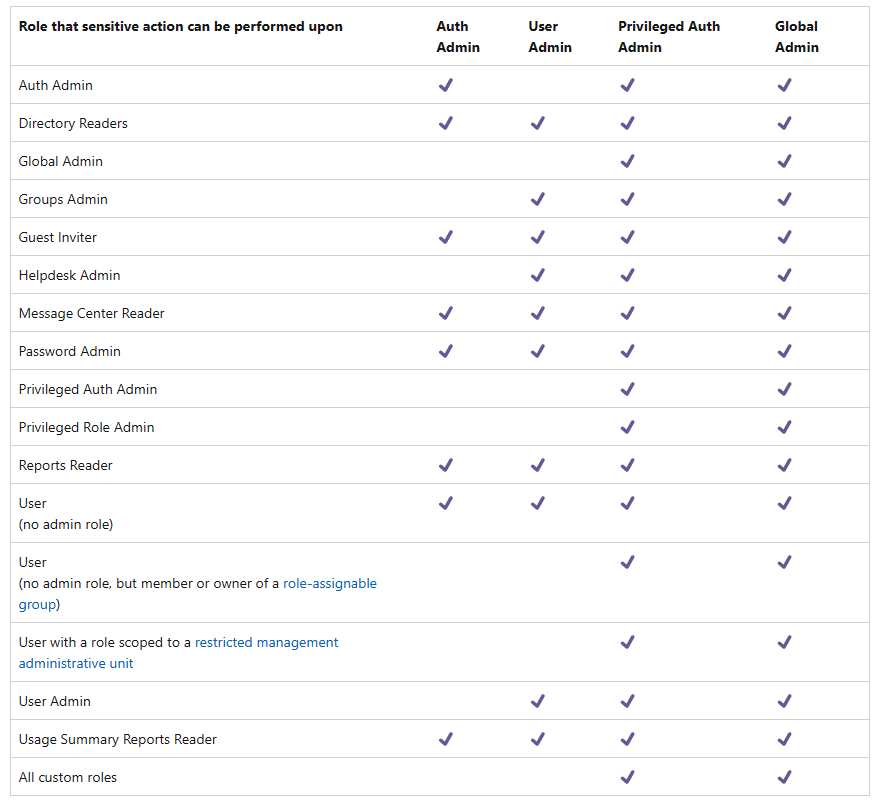
Upon consulting the Microsoft documentation, I discovered that authentication administrators do not have full permissions for all users. Further research unveiled a chart illustrating scenarios where certain users are considered privileged target users, making them unmanageable by normal authentication administrators.
Azure AD built-in roles – Microsoft Entra | Microsoft Learn
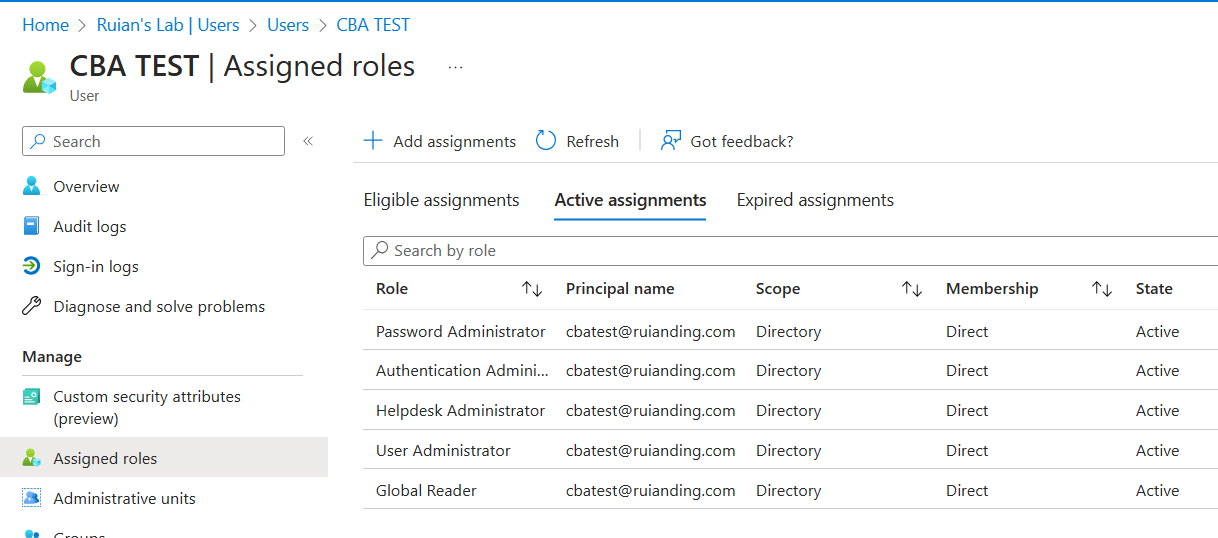
I also noticed a key observation during the investigation. Users without any role assigned, like “test2” appeared to be the primary factor causing the peculiar behavior. Upon close examination, it became apparent that users assigned as members or owners in a group with the “Azure AD roles can be assigned to the group” option enabled were not manageable by non-privileged authentication administrators.
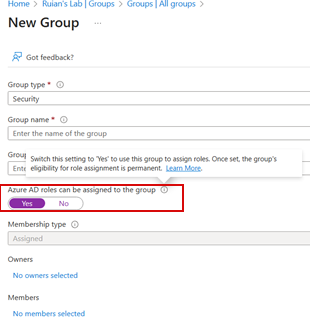
Action Performed
Intrigued to discover more, I delved further into the issue by inspecting the user-assigned groups. I stumbled upon a test group which happened to have the mentioned option enabled, and it included several affected users, including “test2”.
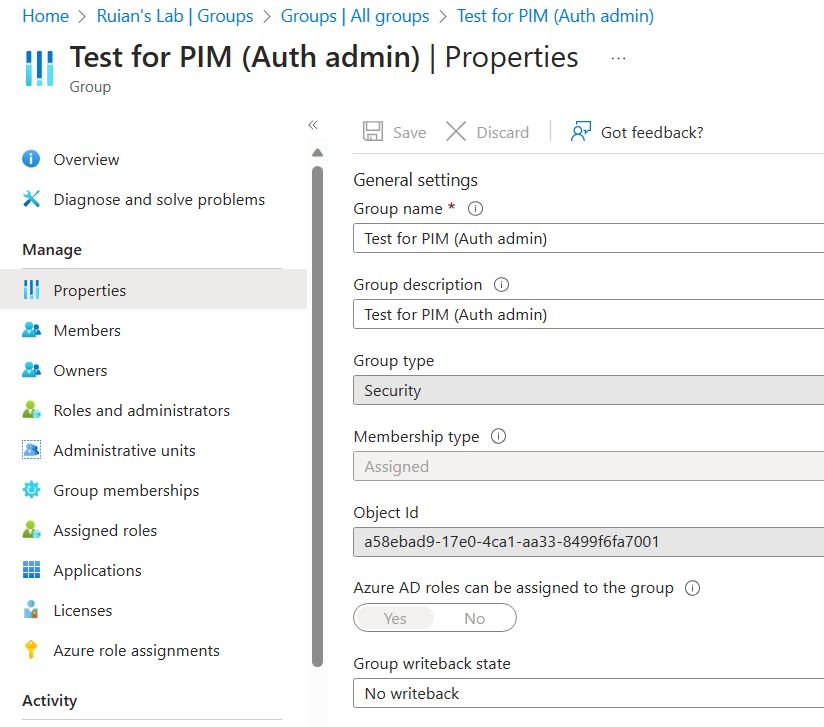
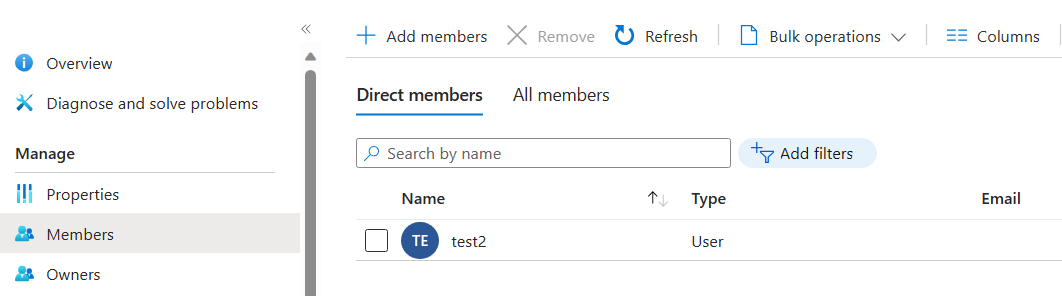
During my investigation, I also learned that the “Azure AD roles can be assigned to group” settings are only configurable when creating a new group and cannot be edited after the group’s creation.
Use Azure AD groups to manage role assignments – Microsoft Entra | Microsoft Learn
Conclusion
Following a comprehensive investigation and analysis, I reached a critical conclusion. The behavior we were encountering was an expected one, rather than a system flaw. Users such as “test,” belonging to groups with the “Azure AD roles can be assigned to the group” option enabled, are considered privileged users. As a result, ordinary authentication administrators, including myself, lacked the required permissions to manage these individuals effectively.
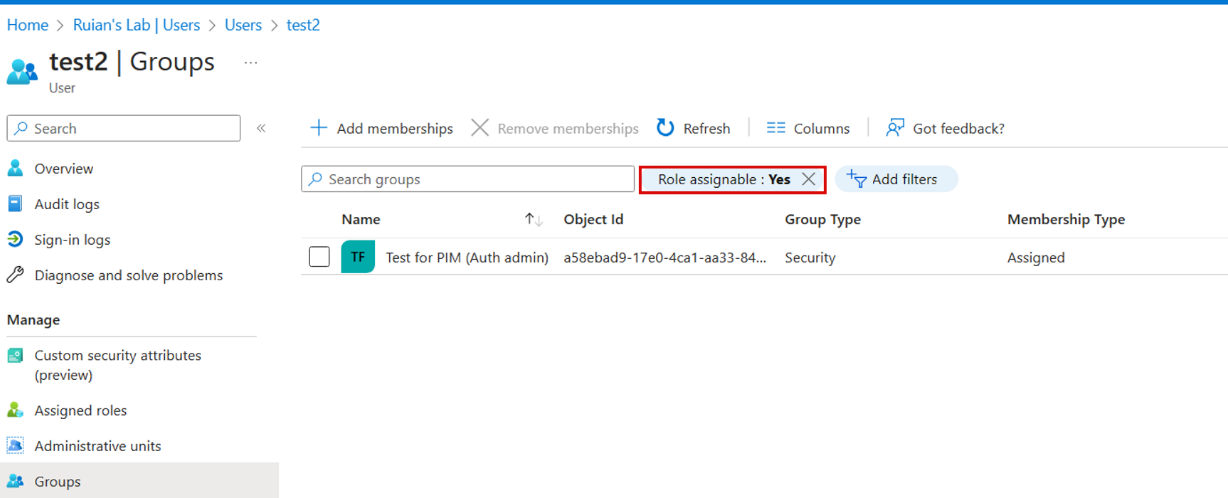
To resolve the issue, we arrived at two potential solutions. The first involves seeking assistance from a higher-privileged administrator to carry out the MFA operations on the affected users. Alternatively, we could consider assigning privileged authentication administrators to handle such tasks. However, the latter option comes with potential security concerns that need to be addressed and evaluated before implementation.
In conclusion, this investigation taught me a valuable lesson about user authentication methods and the impact of group settings on administrative permissions.