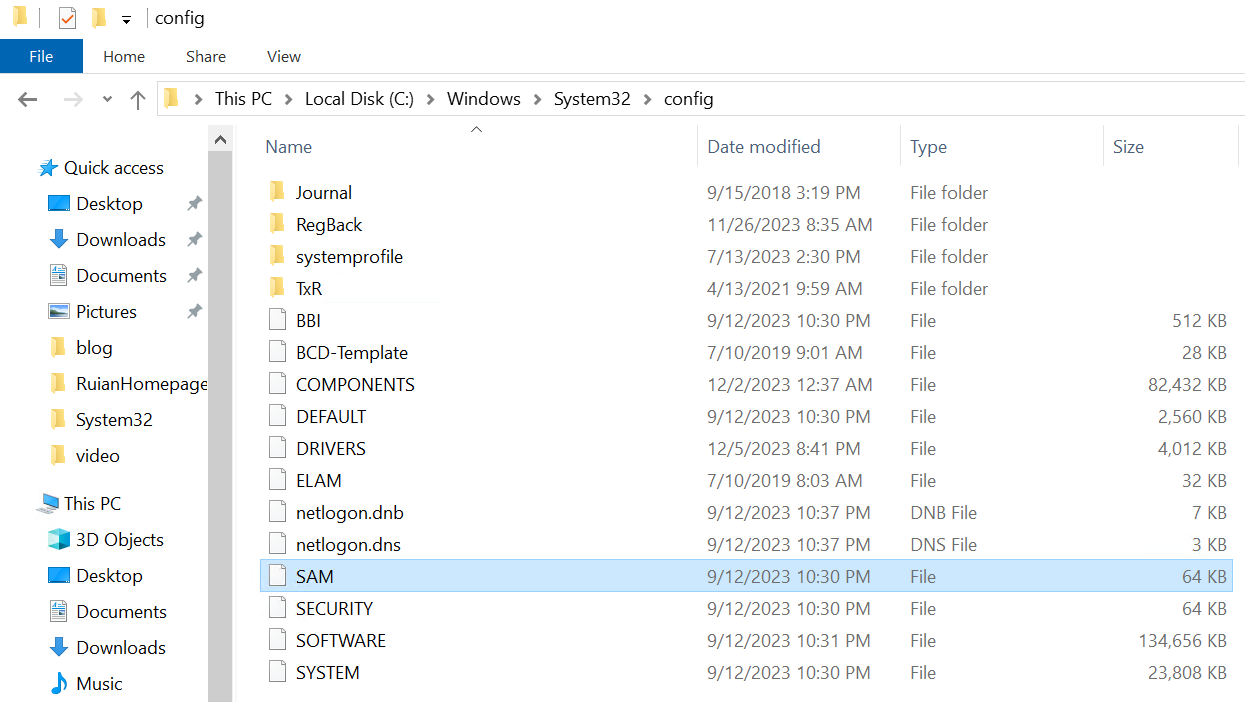
ATT&CK for Enterprise – TA0010 Exfiltration
Exfiltration, Tactic TA0010 – Enterprise | MITRE ATT&CK®
“Exfiltration” in the context of cybersecurity refers to the unauthorized transfer of data from a computer or other device. This tactic, often seen in data breaches and espionage ①, aims to stealthily acquire sensitive information such as personal data, corporate secrets, or intellectual property. Attackers employ various methods for exfiltration, including network transfers, email, physical media like USB drives, or cloud storage services, while prioritizing stealth to evade detection. These acts can closely mimic legitimate network activity, making detection challenging. The consequences of exfiltration are severe, potentially leading to significant data loss, financial and reputational damage, and legal issues. This blog will explore and categorize specific alerts from Other security alerts documentation.
① Espionage refers to the practice of using spies to obtain secret or confidential information without the permission of the holder of the information. It is commonly associated with government and military efforts to gather intelligence on other nations, but it can also occur in corporate settings, known as industrial or corporate espionage.
T1048 Exfiltration Over Alternative Protocol
Adversaries can exfiltrate data using protocols different from their main command and control (C2) channel, potentially also directing the data to a different network location than the primary C2 server. These alternate protocols can include FTP, SMTP, HTTP/S, DNS, SMB, or other network protocols not used for main C2 communication. Adversaries might encrypt or obfuscate these channels. Common operating system utilities like Net/SMB or FTP can facilitate this on various platforms, while tools like curl on macOS and Linux can invoke HTTP/S or FTP/S for data exfiltration. Additionally, IaaS and SaaS platforms like Microsoft Exchange, SharePoint, GitHub, and AWS S3 allow direct downloading of files and sensitive information via web consoles or Cloud APIs, which can be exploited for exfiltration purposes.
| External ID | Name | Sev. | Description |
| 2031 | Suspicious communication over DNS | Medium | Nature of the Attack: The attack involves the use of the DNS protocol by an attacker who has compromised a machine within an organization’s network. Malicious actors can manipulate DNS queries and responses to transmit data covertly. This can be done in several ways, including using DNS requests to communicate with a command and control server, or to exfiltrate data from a compromised network. Data Exfiltration: Stealthily sending sensitive information from the compromised machine to an external server using DNS queries. ① Command and Control: Using DNS queries to receive commands from a remote attacker. This can help in maintaining control over the compromised machine and potentially facilitating further malicious activities. Evading Network Restrictions: DNS is rarely blocked or restricted in corporate networks, allowing attackers to use it to bypass network security measures. |
| 2030 | Data exfiltration over SMB | HIgh | Target and Motive: The primary target in this attack is the domain controller, which holds the most sensitive data within an organization. Attackers aim to gain access to these domain controllers to steal critical information. One of their main objectives is often to acquire the Ntds.dit file ②.Significance of the Ntds.dit File: The Ntds.dit file, stored on the domain controller, is a database that contains all of the information of an Active Directory, including user accounts and passwords.Exfiltration of this file is particularly dangerous because it allows attackers to potentially forge Kerberos TGTs Forging Kerberos TGTs: With forged Kerberos TGTs, attackers can gain unauthorized access to virtually any resource in the network. They can manipulate the ticket expiration to extend their access as long as needed, which significantly elevates the risk and potential impact of the attack. Method of Exfiltration: The data is exfiltrated over SMB ③, a network file sharing protocol. This method involves suspicious transfers of data from the monitored domain controllers, which can be a sign of active exfiltration. |
① “Stealthily sending sensitive information from a compromised machine to an external server using DNS queries” involves embedding sensitive data into DNS requests by malware on the compromised computer. These altered DNS requests, appearing normal, are sent to a DNS server controlled by the attacker. Since DNS requests typically bypass firewall scrutiny due to their essential role in network operations, they can exit the internal network without raising alarms. The attacker’s external DNS server receives these requests and extracts the encoded data. This method is challenging to detect because malicious DNS queries blend in with legitimate traffic, exploiting the general trust in and necessity of DNS communications within networks.
② The NTDS.DIT file is a database file on Windows Active Directory domain controllers that contains all Active Directory data, including user accounts and passwords. Typically, this file is located in the %SystemRoot%\NTDS directory. In most cases, this translates to C:\Windows\NTDS\NTDS.DIT
The NTDS.DIT file, containing sensitive information, is usually not directly visible or accessible to regular users or administrators. To view or access this file, specific system privileges and tools are required. Normally, such operations are only carried out by system administrators during maintenance or under special circumstances.
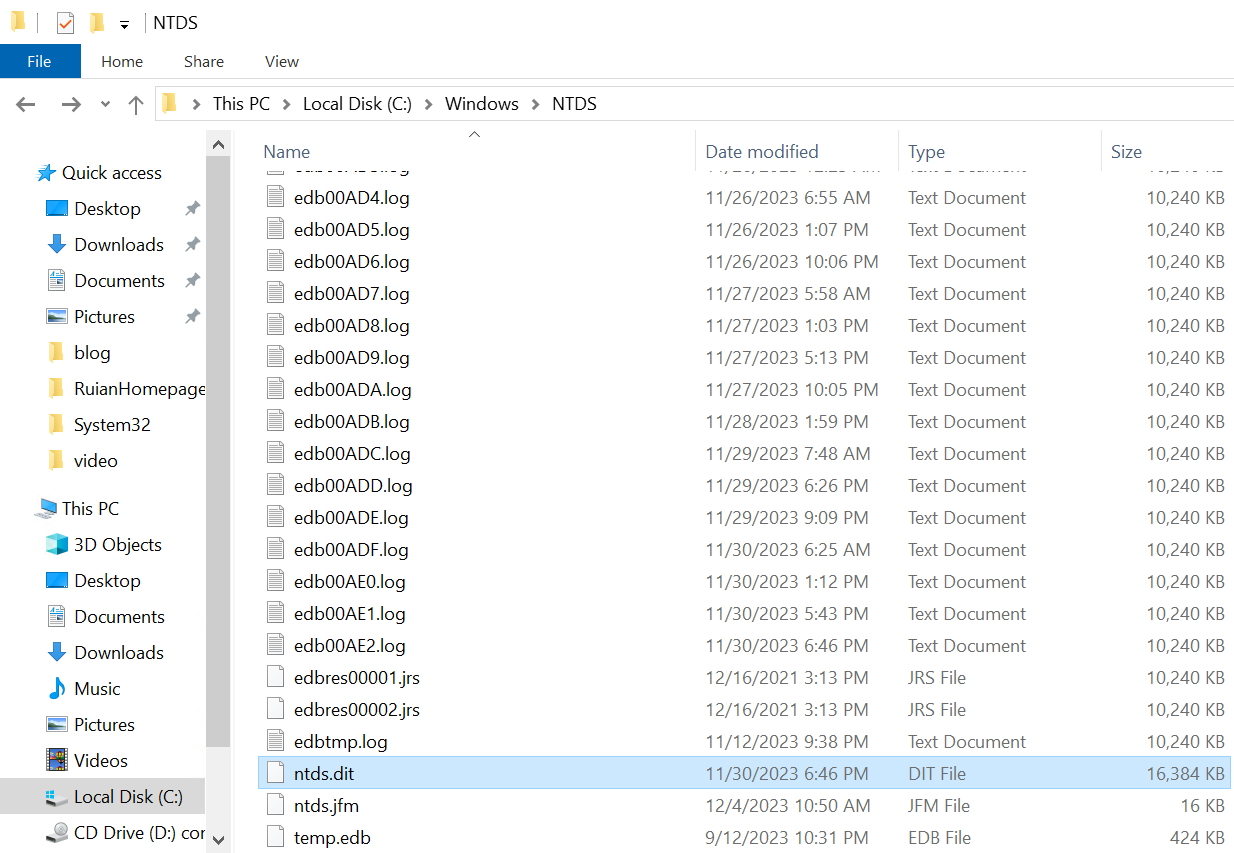
③ In the context of data exfiltration, attackers might utilize the SMB protocol to illicitly transfer data from a domain controller. However, this does not mean that the NTDS.DIT file itself is shared via standard file-sharing methods.
Attackers could potentially access this file by obtaining sufficient privileges or exploiting system vulnerabilities, using SMB as a transport mechanism to move or copy the file or its data from the domain controller to a location under their control.
🔗 The NTDS.DIT file and the SAM file are both important in the context of Windows security, but they serve different purposes and are located in different parts of the system.
NTDS.DIT File: The NTDS.DIT file is a database file located on Active Directory domain controllers. It is a central component of the Windows Active Directory environment, containing comprehensive information about the domain. This includes user accounts, their password hashes (which are encrypted forms of passwords used for authentication), group policies, user rights, and other domain-level data. The password hashes stored in NTDS.DIT are crucial for maintaining security across the domain, as they are used for verifying user credentials during the login process.
SAM File: The SAM file, on the other hand, is located on every Windows computer and stores local user account information. This file contains user account details and password hashes for users on that specific machine. It is used to manage local access to the computer. The SAM file’s scope is limited to the individual system, unlike NTDS.DIT which has domain-wide significance.