ATT&CK for Enterprise – TA0004 Privilege Escalation
Privilege Escalation, Tactic TA0004 – Enterprise | MITRE ATT&CK®
“Privilege Escalation” in cybersecurity refers to tactic where an attacker gains higher-level permissions on a system or network, beyond their original access rights. This can be achieved through vertical escalation, where a user gains elevated privileges (e.g., a regular user obtaining administrative rights), or horizontal escalation, involving access to functions or data reserved for other users at the same privilege level. Attackers employ various methods for this, such as exploiting software vulnerabilities, system misconfigurations, or using stolen credentials. The consequences of successful privilege escalation are significant, leading to unauthorized access, data breaches, and further malicious activities within the network. This blog will explore and categorize specific alerts from Persistence and privilege escalation alerts documentation.
| External ID | Name | Sev. | Description |
| 2411 | Suspected Netlogon privilege elevation attempt (CVE-2020-1472 exploitation) | High | CVE-2020-1472 Vulnerability ②: This is a critical security vulnerability announced by Microsoft in 2020. It affects the Netlogon process, which is a core authentication component of Windows Server operating systems. Netlogon Process: Netlogon ① is a service that facilitates user and machine authentication in Windows domain environments. It’s essential for the security and management of domain controllers, which are servers that handle security authentication requests within a Windows domain. Nature of the Vulnerability: The vulnerability allows attackers to exploit the Netlogon Remote Protocol (MS-NRPC) ② to elevate their privileges to that of a domain controller, which is the highest administrative level in a Windows domain. It involves establishing a vulnerable connection to a domain controller using MS-NRPC, a core protocol used by the Netlogon service. Impact of Exploitation: Exploiting this vulnerability grants an attacker significant control over the domain network. They can potentially add new accounts, change or delete data, access sensitive information, and spread malware. |
| 1106 | Suspected SID-History ③ injection | High | Normal Use of SIDHistory: During a legitimate account migration, the user’s original SID from the old domain is added to the SIDHistory attribute of their account in the new domain. This attribute then contains a list of SIDs that represent the user’s identity in previous domains, allowing for seamless access to resources that were permissions-granted under the old SID. SID-History Injection: Attackers exploit this feature by injecting a SID into the SIDHistory attribute of an account in the target domain. This is typically done by adding a SID that has elevated privileges in the domain. By injecting a SID with higher privileges (like that of an administrator) into the SIDHistory of a regular user account, attackers can escalate their privileges in the new domain. Consequences of the Attack: The injected SID allows the attackers to bypass access controls and gain permissions they would not normally have. This could lead to unauthorized access to sensitive data, modification of critical settings, or further exploitation of the domain resources. |
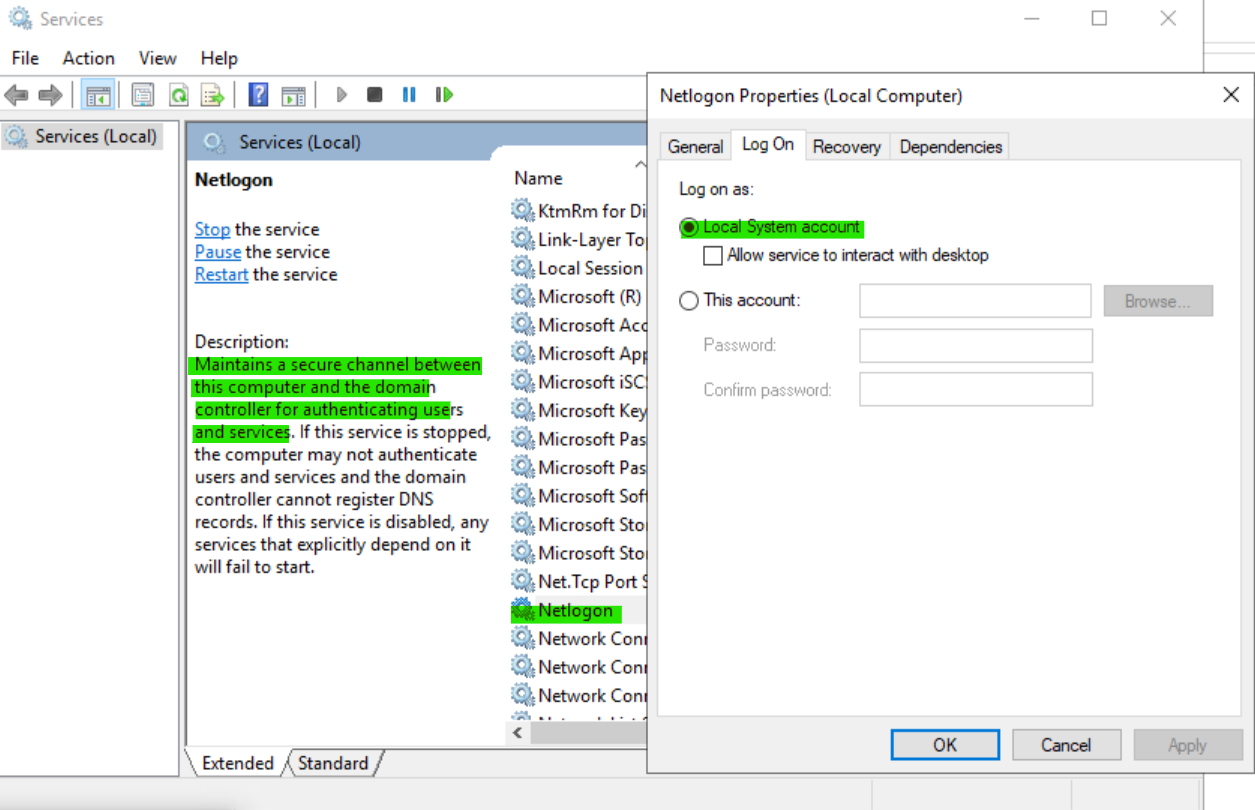
① The Netlogon service is an essential component in Windows domain networks, primarily running on domain controllers, but it also plays a role in domain-joined machines.
The Netlogon service is integral in setting up and maintaining these secure channels. It’s not the service that directly handles user authentication (like verifying user credentials), but it facilitates the process by establishing a secure communication path between the domain controller and the client.
② CVE-2020-1472 Vulnerability exists in the Netlogon remote protocol (MS-NRPC), a protocol used for operations such as updating computer passwords. Normally, when a domain-joined computer communicates with a domain controller, they use a complex encryption process to ensure the security of the communication. However, this vulnerability allows attackers to send incorrect encryption values (specifically, a series of zero values), and the domain controller erroneously accepts this encryption value.
Exploiting this vulnerability, attackers can forge the identity of a domain-joined computer and establish a secure channel with the domain controller. Once a secure channel is established, attackers can use this trust relationship to execute various commands, such as changing passwords. Since attackers can control communication with the domain controller, they can elevate their privileges, gaining the same access rights as the domain controller and thus gaining control over the entire domain.
③ SIDHistory is an attribute in Active Directory that retains a user’s Security Identifier (SID) from a previous domain when their account is migrated to a new domain. It ensures that users maintain their permissions and access to resources despite the domain change.
The following command can help query the SIDHistory attribute. However, it is necessary to confirm whether the account has been migrated from another domain and if the SID from the old domain was retained during the migration process. If the account has never been migrated, it likely does not have a SIDHistory attribute.Get-ADUser -Identity <username> -Properties sidhistory | Select-Object Name, SIDHistory