AAD General FAQs
AAD Overview
Q1. What’s Azure Active Directory? What’s the key benefits? How many editions does it have? Why we need these editions?
Azure Active Directory (Azure AD) is Microsoft’s cloud-based identity and access management service. It provides a comprehensive set of capabilities to manage user identities, control access to resources, and enable secure authentication and authorization across various applications and services.
Key benefits of Azure Active Directory include:
Single sign-on (SSO): Users can sign in once to Azure AD and then access multiple applications and services without the need for separate credentials. This improves user productivity and reduces password-related issues.
What is single sign-on? – Microsoft Entra | Microsoft Learn
Centralized identity management: Azure AD allows organizations to manage user identities, groups, and access policies in a centralized manner. It provides features for user provisioning, self-service password reset, and group-based access control.
Multi-factor authentication (MFA): Azure AD supports various MFA methods, such as SMS, phone call, or mobile app verification, to add an extra layer of security to user sign-ins.
Azure AD Multi-Factor Authentication overview – Microsoft Entra | Microsoft Learn
Application management: Azure AD enables organizations to securely manage access to their applications, whether they are hosted in the cloud or on-premises. It provides features like application registration, single sign-on integration, and user access reviews.
What is application management? – Microsoft Entra | Microsoft Learn
B2B and B2C scenarios: Azure AD supports business-to-business (B2B) collaboration scenarios, allowing organizations to grant access to external partners or customers. It also offers Azure AD B2C, which is designed for customer-facing applications that require identity management for external users.
Azure Active Directory has several editions, each designed to cater to specific organizational requirements. The editions include:
Azure Active Directory | Microsoft Azure
Free Edition: This edition provides basic identity and access management capabilities for up to 50,000 directory objects (users, groups, and contacts). It includes features like user and group management, single sign-on for cloud applications, and self-service password reset.
Office 365 Apps Edition: This edition is designed for organizations using Office 365 applications. It includes all the features of the Free Edition and provides additional capabilities for Office 365 services.
Premium P1 Edition: This edition offers advanced identity protection, access management, and security features. It includes features like conditional access policies, self-service group management, advanced reporting, and Azure AD Identity Protection.
Premium P2 Edition: This is the most comprehensive edition, providing all the features of the Premium P1 Edition along with additional capabilities such as Azure AD Identity Governance, privileged identity management, and Microsoft Identity Manager.
Q2. What’s the relationship between Azure subscription, O365, Dynamics CRM Online, EMS or other Microsoft cloud services with Azure AD tenant?
Azure Active Directory serves as the underlying identity and access management service for various Microsoft cloud services, including Azure subscriptions, Office 365 (O365), Dynamics CRM Online, Enterprise Mobility + Security (EMS), and more. Azure AD acts as the directory service that manages user identities, authentication, and authorization for these cloud services.
Q3. What authentication protocols does AAD support?
Security Assertion Markup Language (SAML): AAD can act as a SAML identity provider (IdP), allowing users to authenticate to applications and services that support SAML-based authentication. SAML enables single sign-on (SSO) between different systems and simplifies user authentication by exchanging XML-based security assertions.
OAuth 2.0: AAD supports OAuth 2.0, an open standard for authorization. It enables applications to obtain access tokens from AAD to access protected resources on behalf of a user. OAuth 2.0 is commonly used for scenarios like granting permissions to third-party applications and enabling delegated access to APIs.
OpenID Connect: AAD is an OpenID Connect (OIDC) provider, which is an authentication layer built on top of OAuth 2.0. OIDC enables clients (such as web or mobile applications) to authenticate users and obtain identity information in the form of JSON Web Tokens (JWTs). It provides features like SSO, user authentication, and identity claims.
WS-Federation: AAD supports the WS-Federation protocol, which is a web services protocol used for exchanging security tokens between a security token service (STS) and a web service. WS-Federation enables SSO across different systems and federated authentication scenarios.
Kerberos and NTLM: AAD supports Kerberos and NTLM authentication protocols for scenarios where users need to authenticate using Windows domain credentials. This allows seamless integration with on-premises Active Directory environments and enables users to access cloud resources without the need for separate credentials.
Certificate-based authentication: AAD supports authentication using client certificates. Applications can use X.509 certificates to authenticate themselves to AAD, providing a secure means of authentication.
Q4. What’s the relationship between O365 and AAD?
AAD provides the foundational identity and access management capabilities for Office 365. It manages user identities, enables authentication and SSO, allows administrators to control access and security settings, and integrates with other Azure services to enhance the overall productivity and security of Office 365 environments.
AAD Identity Management
Q1. How many AAD admin roles does AAD has?
AAD has several built-in admin roles that provide different levels of access and control over the AAD resources and user accounts.
Azure AD built-in roles – Microsoft Entra | Microsoft Learn
Q2. What’s Self-service Password Change/Reset? What’s the license requirement for sync user and cloud user?
Self-service Password Change/Reset (SSPR) allows users to change or reset their passwords without contacting IT support.
Enable Azure Active Directory self-service password reset – Microsoft Entra | Microsoft Learn
The license requirement for sync users from on-premises Active Directory to Azure AD depends on the features you want to use. Azure AD Premium P1 or P2, or a Microsoft 365 license with Azure AD Premium, typically includes Azure AD Connect for synchronization.
Q3. What’s Self-service group management? What’s the license requirement for this feature?
Self-service group management in Azure Active Directory allows users to create and manage security groups without IT support. Basic group management is available to all users, while advanced features may require an Azure AD Premium license (P1 or P2) or a Microsoft 365 license with Azure AD Premium.
Set up self-service group management – Microsoft Entra | Microsoft Learn
Q4. What does AAD Connect do?
Azure AD Connect is a Microsoft tool used to synchronize on-premises Active Directory (AD) identities and attributes with Azure Active Directory (AAD). It enables organizations to integrate their on-premises AD infrastructure with Azure AD, providing a unified identity and access management experience for both on-premises and cloud-based resources.
The main functions of Azure AD Connect include:
Directory Synchronization: Azure AD Connect synchronizes user accounts, groups, and other directory objects from the on-premises AD to Azure AD. This ensures that user identities and attributes are consistent across both environments.
Password Hash Synchronization: This feature synchronizes user passwords from on-premises AD to Azure AD, allowing users to use the same password for authentication in both environments.
Federation Integration: Azure AD Connect supports federation scenarios, enabling organizations to establish trust relationships between their on-premises AD and Azure AD. This facilitates single sign-on (SSO) and seamless access to cloud-based applications.
Seamless Single Sign-On (SSO): Azure AD Connect enables SSO for users accessing Azure AD-integrated applications from domain-joined devices. This eliminates the need for users to enter their credentials multiple times.
Customization and Filtering: The tool provides customization options to filter objects and attributes during synchronization, allowing organizations to control which data is synchronized and which attributes are visible in Azure AD.
AAD Domain and Tenant Management
Q1. What’s Microsoft account, work account, email as sign in account? What’s the URL handing the authentication request?
Microsoft Account: A Microsoft Account is a personal account provided by Microsoft that allows users to sign into a wide range of Microsoft services, such as Outlook.com, OneDrive, Xbox Live, and Microsoft Store. It is typically associated with a personal email address, such as Outlook.com, Hotmail.com, or Live.com.
Authentication request URL: login.microsoftonline.com
Work Account: A Work Account, also known as an Organizational Account, is an account provided by an organization or employer using Azure Active Directory . It allows users to access organizational resources, such as Microsoft 365, Azure services, and other work-related applications. Work Accounts are associated with the user’s work or school email address.
Authentication request URL: login.live.com
Email as Sign-In Account: Email as Sign-In Account refers to the option of using an email address as the username for signing into Microsoft services. This can apply to both Microsoft Accounts and Work Accounts, where the email address serves as the primary identifier for authentication.
Q2. What’s the relationship of Azure AD and Azure Subscription?
An Azure AD tenant is not subordinate to an Azure subscription, but rather, an Azure subscription belongs to an Azure AD tenant. Users, groups, and applications authorized to access an Azure subscription must exist in the same Azure AD tenant.
The Global Administrator role in Azure AD does not grant access to Azure subscriptions by default. However, a Global Admin in an Azure AD tenant can grant themselves access to Azure subscriptions within that same tenant.
Users can create new Azure AD tenants, and when they do, they become external users in the new tenant’s Global Admin role. The new tenant has no direct relationship with any Azure subscriptions initially.
Referencing the blog post from Microsoft EEE: Demystifying the relationship of Azure AD and Azure Subscription. – TheIdentityGuy (wordpress.com)
Q3. How to transfer Azure tenant for an Azure Subscription?
Please note that transferring an Azure tenant requires assistance from Azure support, as it involves administrative actions that must be carefully managed to maintain data security and access control.
Here is the link to Microsoft’s documentation that provides step-by-step instructions for the tenant transfer process:
Transfer an Azure subscription to a different Azure AD directory | Microsoft Learn
Q4. What’s verified domain? How does Microsoft know the domain belongs to this customer?
A verified domain in the context of Azure Active Directory (Azure AD) is a domain that has been confirmed and associated with an organization or customer. When a domain is verified, it demonstrates that the customer has ownership and control over the domain.
To verify a domain, Microsoft employs a variety of methods to ensure that the domain belongs to the customer:
Domain ownership verification: Microsoft may request the customer to add a specific DNS record or a TXT record to their domain’s DNS configuration. This record acts as proof of domain ownership. Microsoft’s systems can then verify the presence of this record to confirm that the customer has control over the domain.
Add and verify custom domain names – Microsoft Entra | Microsoft Learn
Other sort of verification methods may include, Email-based verification, File-based verification, Third-party domain provider verification (Require assistance from Azure support).
By employing these methods, Microsoft ensures that only authorized individuals or organizations can claim and verify domains within Azure AD. This verification process helps maintain security, prevents unauthorized domain usage, and establishes trust between Azure AD and the domain owners.
AAD Reporting
Q1. How many AAD reports under Activity section do we have?
It’s recommended to refer to Microsoft’s official documentation or the Azure portal for the most up-to-date information on the available reports and their functionality.
What are Azure Active Directory reports? – Microsoft Entra | Microsoft Learn
Sign-ins: This report provides information about user sign-ins to Azure AD and associated details like sign-in time, location, client application used, and result (success, failure, or conditional access).
Audit logs: This report provides a comprehensive record of activities and events within Azure AD, including sign-ins, user management actions, application access, and more. It allows administrators to monitor and investigate activities in their directory.
Risky sign-ins: This report focuses on sign-ins that are flagged as risky based on Azure AD’s built-in risk detection mechanisms. It helps administrators identify potential security threats and take appropriate actions.
Q2. What’s the retention of each AAD reports?
Azure Active Directory data retention – Microsoft Entra | Microsoft Learn
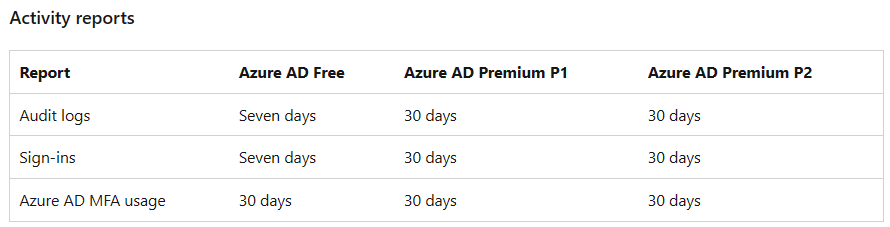
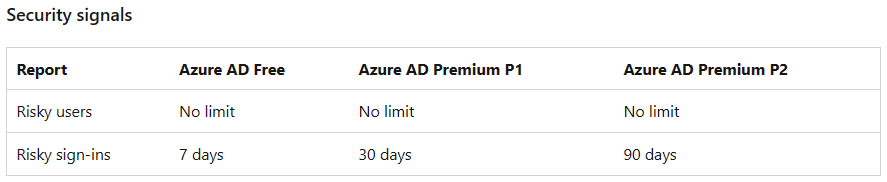
It’s important to note that Microsoft may update their services and policies, including retention periods, over time.
Q3. What’s the license requirement for AAD reports?
Referring to the previous question.
Q4. Who can access activity sign-ins report?
Access to the activity sign-ins report is typically limited to users with appropriate permissions. By default, only users with the Global Administrator or Security Administrator roles have access to view the sign-ins report. These roles have high-level privileges and are responsible for managing and securing the Azure AD environment.
Azure AD built-in roles – Microsoft Entra | Microsoft Learn
However, Azure AD allows administrators to delegate access to specific reports to other users or roles. This can be done through role-based access control (RBAC) in Azure AD. By assigning the appropriate RBAC roles, administrators can grant access to the activity sign-ins report to specific users or groups.
AAD Sign-in Options
Q1. What’s the general authentication workflow for Password sync auth, federation auth, Pass-through auth? What’s the domain type for each method (managed or federated)?
- Password Hash Sync Authentication (PHS):
- Domain Type: Managed domain
- Workflow:
- User enters their username and password.
- The user’s password is synchronized from the on-premises Active Directory (AD) to Azure AD using Azure AD Connect.
- Azure AD validates the user’s credentials against the synchronized password in Azure AD.
- If the credentials are valid, the user is granted access to the requested resource.
- Pass-through Authentication (PTA):
- Domain Type: Managed domain
- Workflow:
- User enters their username and password.
- The user’s password is sent to the on-premises agent (Azure AD Connect) deployed in the organization’s environment.
- The agent verifies the user’s credentials against the on-premises AD.
- If the credentials are valid, the agent sends the verification result to Azure AD.
- Azure AD grants access to the requested resource based on the verification result.
- Federation Authentication:
- Domain Type: Federated domain
- Workflow:
- User enters their username and selects their identity provider (IdP).
- The user is redirected to their IdP (such as Active Directory Federation Services – ADFS).
- The IdP authenticates the user against the on-premises AD or other identity system.
- Upon successful authentication, the IdP generates a security token.
- The user is redirected back to Azure AD with the security token.
- Azure AD validates the security token and grants access to the requested resource.
In summary, Password Sync Authentication uses a synchronized password in Azure AD, Federation Authentication leverages an identity provider (IdP) for authentication, and Pass-through Authentication validates user credentials against the on-premises AD. The domain type is typically “Managed” for Password Sync and Pass-through Authentication, while “Federated” domain types are associated with Federation Authentication.
Like!