Enable Web Sign-in with Temporary Access Pass
Overview
This post will share how to implement Web Sign-in Feature, and this feature will allow the user sign-in Windows with the TAP (Temporary Access Pass).
As the reminder, the Web Sign-in feature used to be the feature that can support 3rd party federation sign-in and MFA. For example, AAD Joined machine only supports 3rd party IDP with WS-TRUST protocol, and 3rd party such as Google IDP will not able to login Windows due to its federation protocol is SAML2. However, with Web Sign-in feature, user would be able to sign-in since an embedded browser looking window will pop up. And it is different from the normal Windows Sign-in, and the limitation due to the federation protocol will no longer exist.
Besides, due to Windows Sign-in is considered as non-interactive, and the interactive MFA will not be supported. The web sign-in can also mitigate this limitation, which allows user to do MFA in the embedded browser window.
However, the bad news is Web Sign-in is not a public released feature and Microsoft Product team has already disabled this private preview feature. Currently, only Temporary Access Pass could be used in order to sign-in windows. Refering below Microsoft Documentation:
What’s new in Windows 10, version 1809 – What’s new in Windows | Microsoft Learn
Nevertheless, we still can use the Web Sign-in feature with TAP. The down below sections will provide the instructions to configure the Web Sign-in and TAP.
1. What is Temporary Access Pass?
Please refer below Microsoft Documentation for the introduction to TAP.
Configure a Temporary Access Pass in Azure AD to register Passwordless authentication methods – Microsoft Entra | Microsoft Learn
Here’s the definition for TAP:
A Temporary Access Pass is a time-limited passcode that can be configured for multi or single use to allow users to onboard other authentication methods including passwordless methods such as Microsoft Authenticator, FIDO2 or Windows Hello for Business.
TAP could be considered as a strong authentication method such as passwordless. In other words, once the user authenticated via TAP, both primary and secondary authentication will be satisfied. This post will not go into too much detail about other TAP application scenarios. Below is one of the implemation of the TAP. Secure authentication method provisioning with Temporary Access Pass – Microsoft Tech Community
2. Instructions of Configuring Web Sign-in
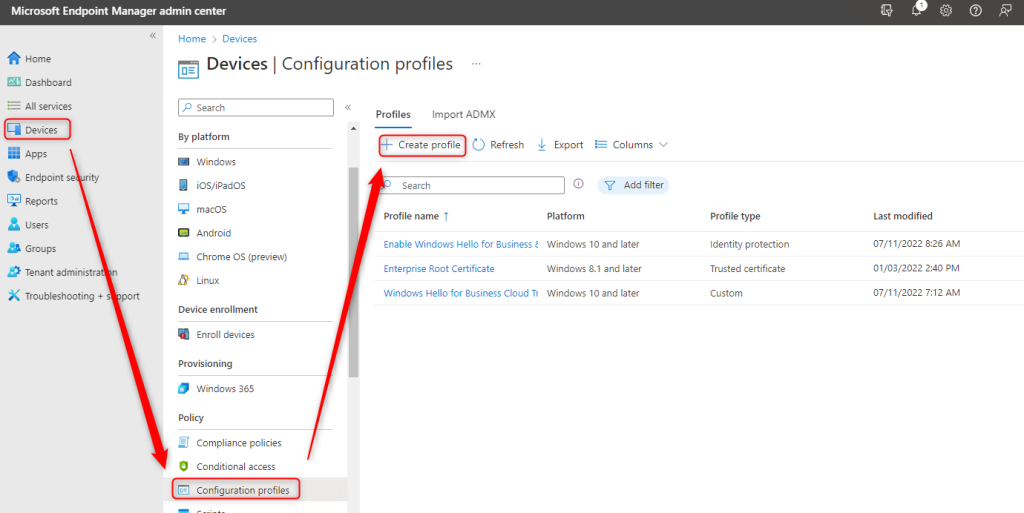
1. Sign-in to the Microsoft Endpoint Manager admin center (Intune Portal).
2. Select Devices > Configuration profiles > Create profile.
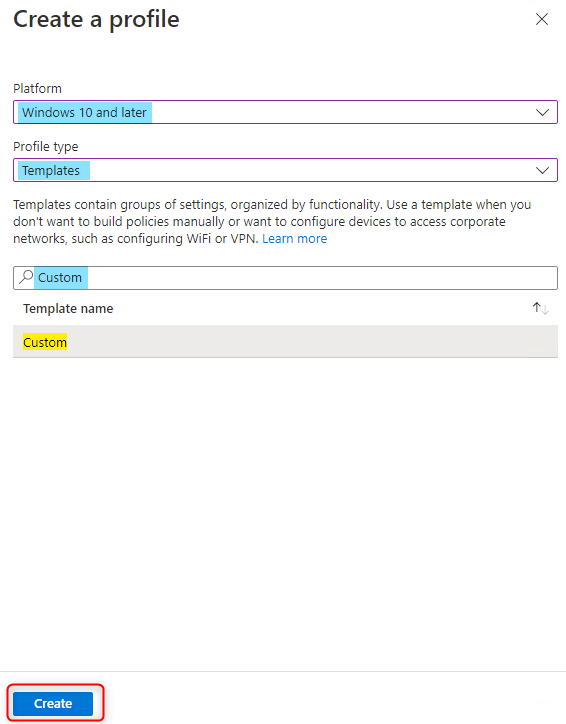
3. Choose Windows 10 and later as the Platform; Templates as the Profile type; Custom as the template name. > Click Create
4. Give the policy a Name > Click Next
5. Add the custom rules as below under Configuration settings, add the OMA-URI Settings:
Name: Web Sign In
OMA-URI: ./Device/Vendor/MSFT/Policy/Config/Authentication/EnableWebSignIn
Data Type: Integer
Value: 1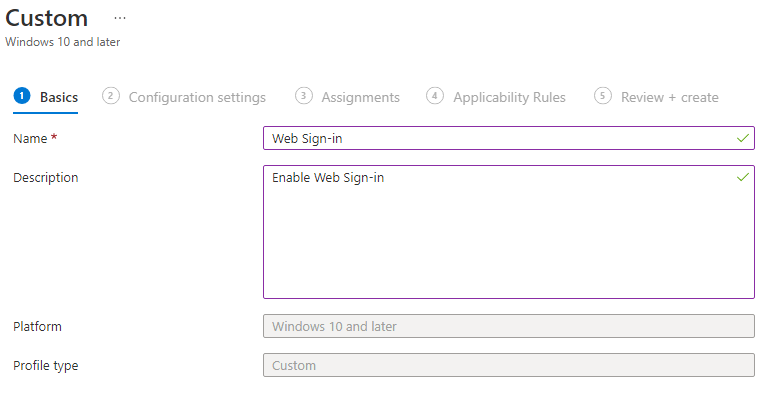
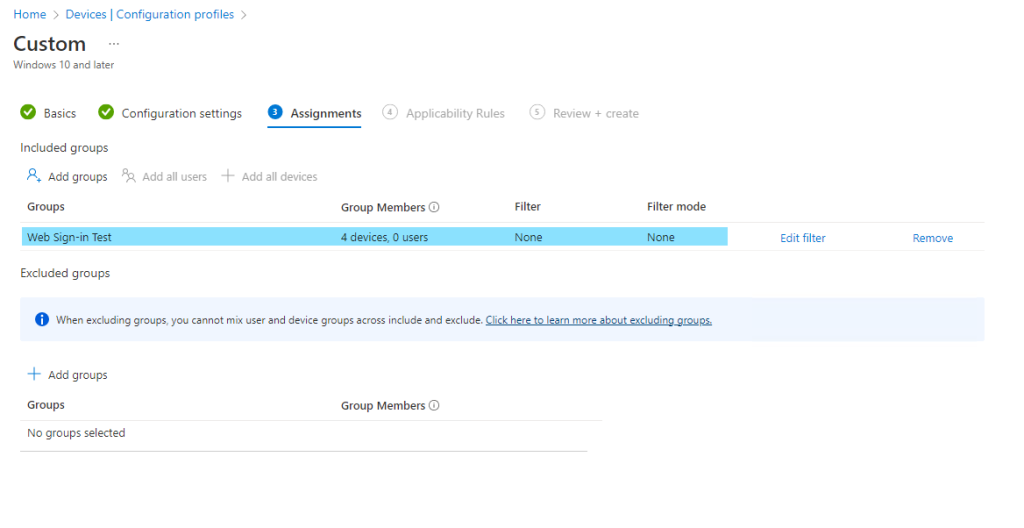
6. Assign this policy to the group who has enrolled their devices with Intune. Create the policy, then wait for the policy to apply to the devices.
3. Instructions of setting up Temporary Access Pass
3.1 Enable Temporary Access Pass for your AAD tenant
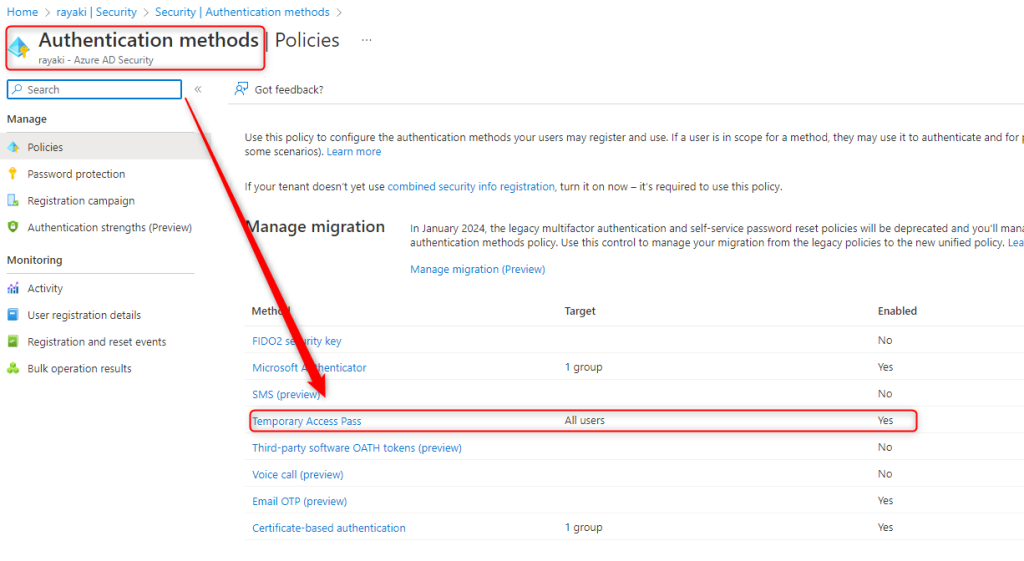
1. Sign-in to the Azure Active Directory.
2. Select Security Blade > Authentication methods > Enable the users/groups that you wants to apply the TAP:
3.2 Create the Temporary Access Pass
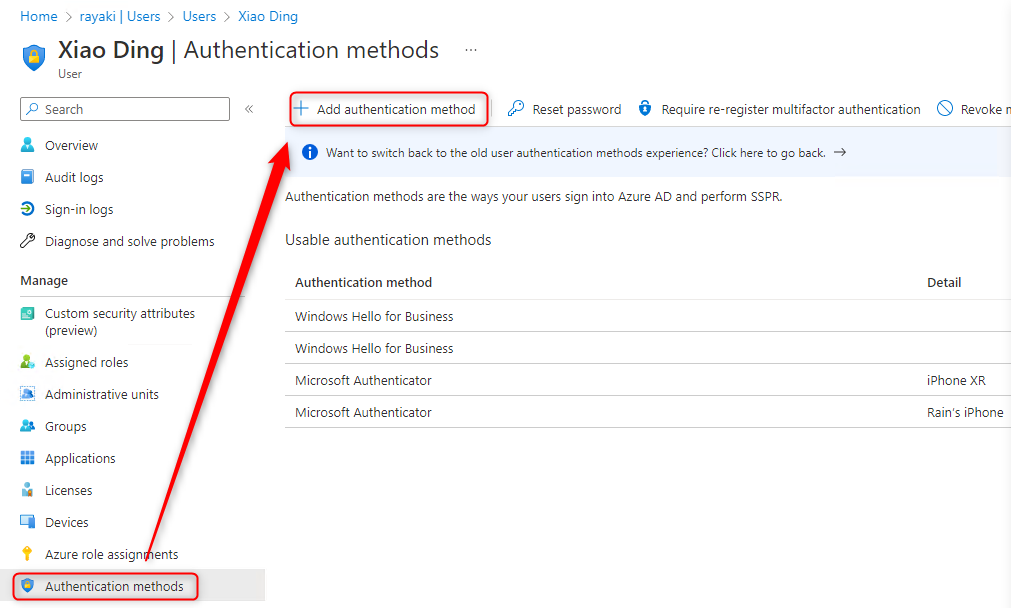
1. Go to Users Blade > Select the targeted user > Click Authentication methods > Add authentication method
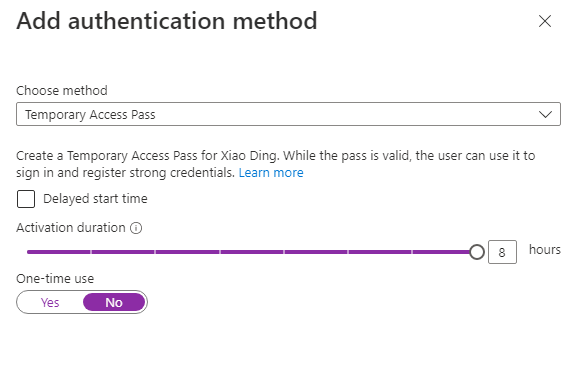
2. Choose Temporary Access Pass as the method, customize the settings that you want > Then Add
3. You will be able to see the TAP after you click Add.
4. Copy & Save the Pass for further use.
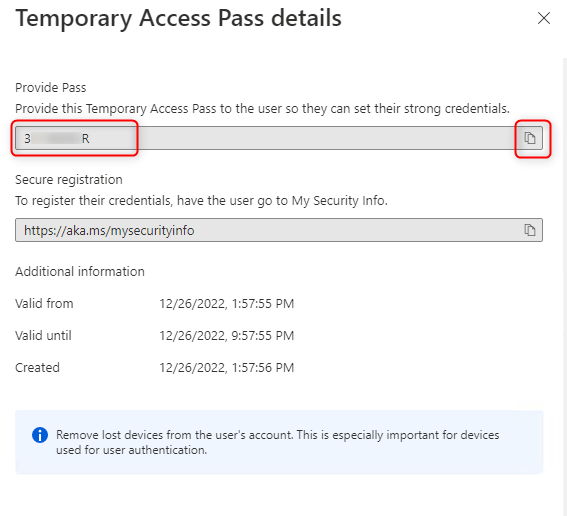
4.Test the Windows Web Sign-in with your TAP
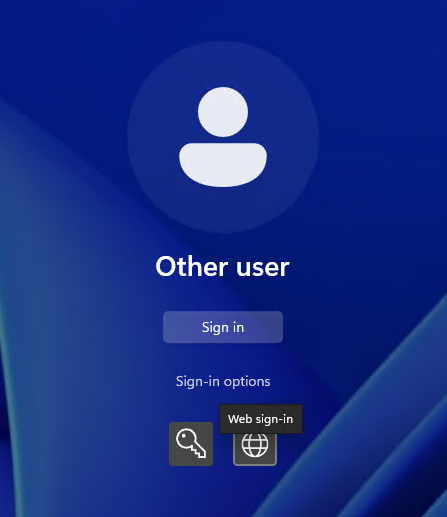
1. Click Sign-in Options > Click Web Sign-in Icon > Click Sign-in After
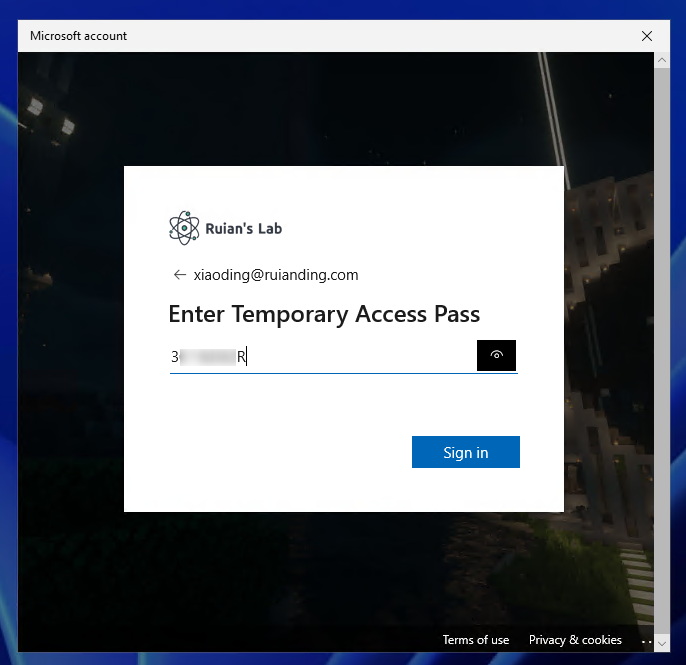
2. Enter your Azure AD UPN > Enter the TAP we created on previous steps.
3. Congratulations, you are signed in.
5.Deep Dive
5.1 Does the PRT contain MFA claim with TAP web sign-in?
As can be seen below, the once we sign-in with the TAP, our credential type is NGC (Next Generation Credential), which equivalent to WHfB sign-in. And as tested, the PRT contained the MFA claim and user will not be challenged to do MFA anymore.
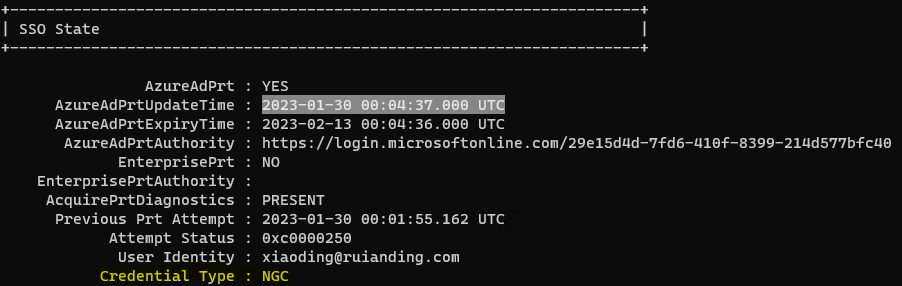
As mentioned before, once the user authenticated via TAP, both primary and secondary authentication will be satisfied. In this case, we can conclude more that this also applies to Windows Web sign-in using TAP.
5.2 Can Hybrid Azure AD Joined device use the TAP to sign-in?
The conclusion is that TAP is not supported for Hybrid Azure AD joined device.
For HAADJ device, after Intune policy applied to the device, we could also see the Web Sign-in option. However, after the sign-in finished. User will not able to login to windows and it will switch back to the sign-in options UI.
I suspect that we have done the authentication to AAD via TAP, but we are missing some mechanism with authentication to on-prem Domain Controller/Kerberos provider since the primary authority for authentication of Hybrid Azure AD join device would still be on-prem DCs.
Like WHfB, it offers 3 trust types in order to connect authentication between the Cloud AAD and on-prem AD.
All in all, based on my testing and understanding of device registration, TAP Web sign-in now seems to be unsuitable for hybrid-joined devices because it doesn’t have the same mechanism as WHfB or FIDO2 key which look for on-prem KDC authentication.