Troubleshooting the Backup of BitLocker Keys to Azure AD
Overview
Once the device is registered to Azure Active Directory (AAD), AAD provides an option to securely store the BitLocker recovery key within the AAD database.

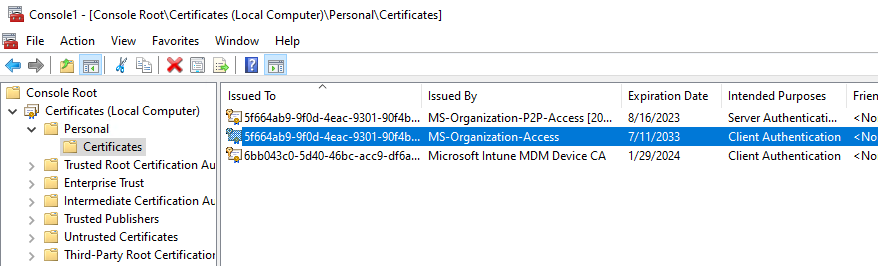
AAD will provide the device with a certificate that is stored in the computer’s certificate store (for AAD-registered devices, the certificate is in the user store). This certificate’s subject name matches the AAD device ID, and it is issued by MS-Organization-Access.
To securely store the recovery key in AAD, the client machine needs to communicate with the https://enterpriseregistration.windows.net/ endpoint. During this process, the client machine sends its key ID along with the recovery key. To establish its identity, the client needs to present its device certificate to this endpoint. To capture this uploading process for analysis, you can use tools like Fiddler.
1. SSL Related Issue
1.1 Monitoring the Entire Flow Using Fiddler
When enabling Fiddler’s capture feature, there’s a possibility of disrupting client certificate authentication, leading to a persistent HTTP 401 error.
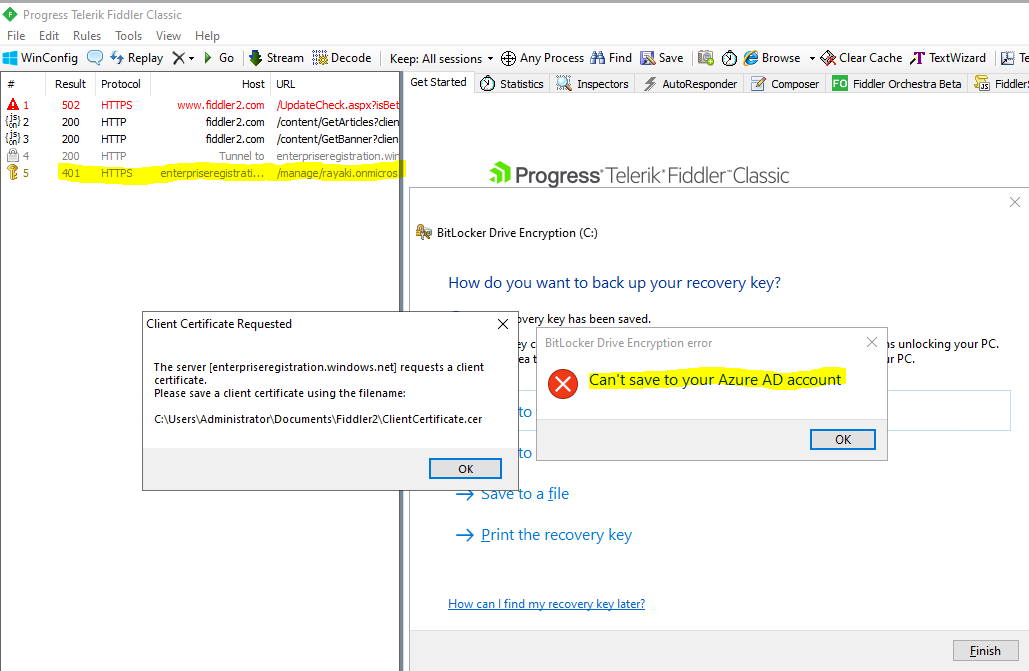
To effectively capture Fiddler traces without this issue, it’s necessary to save the device certificate as ‘ClientCertificate.cer’ in the following path: %USERPROFILE%\My Documents\Fiddler2\ClientCertificate.cer
This action enables Fiddler to automatically select the correct device certificate for the process.
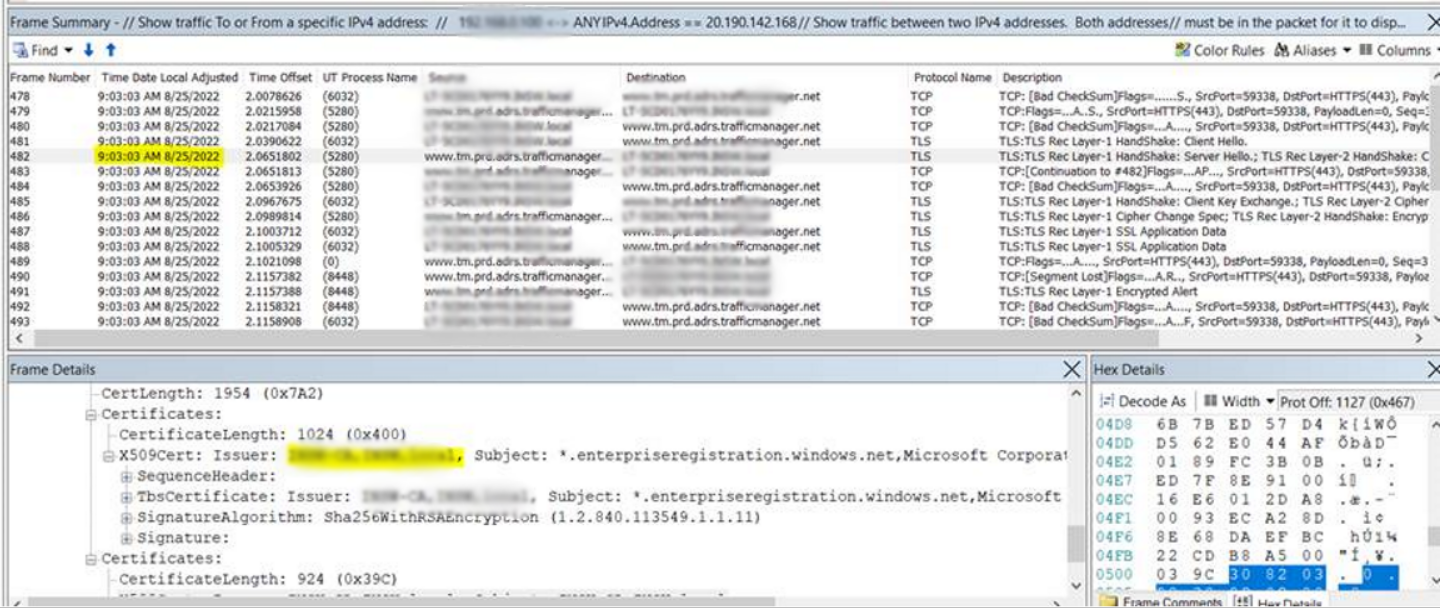
1.2 The certificate issuer has been tampered with by the SSL inspector
I’ve encountered a situation where, while establishing a TLS handshake with the DRS endpoint, it became apparent from the Server Hello frames that an intermediary network device or proxy server was involved. This interference resulted in the alteration of the issuer information in the device certificate returned by the Server Hello. This alteration was responsible for the failure of BitLocker key backup as well.