ATT&CK for Enterprise – TA0005 Defense Evasion
Defense Evasion, Tactic TA0005 – Enterprise | MITRE ATT&CK®
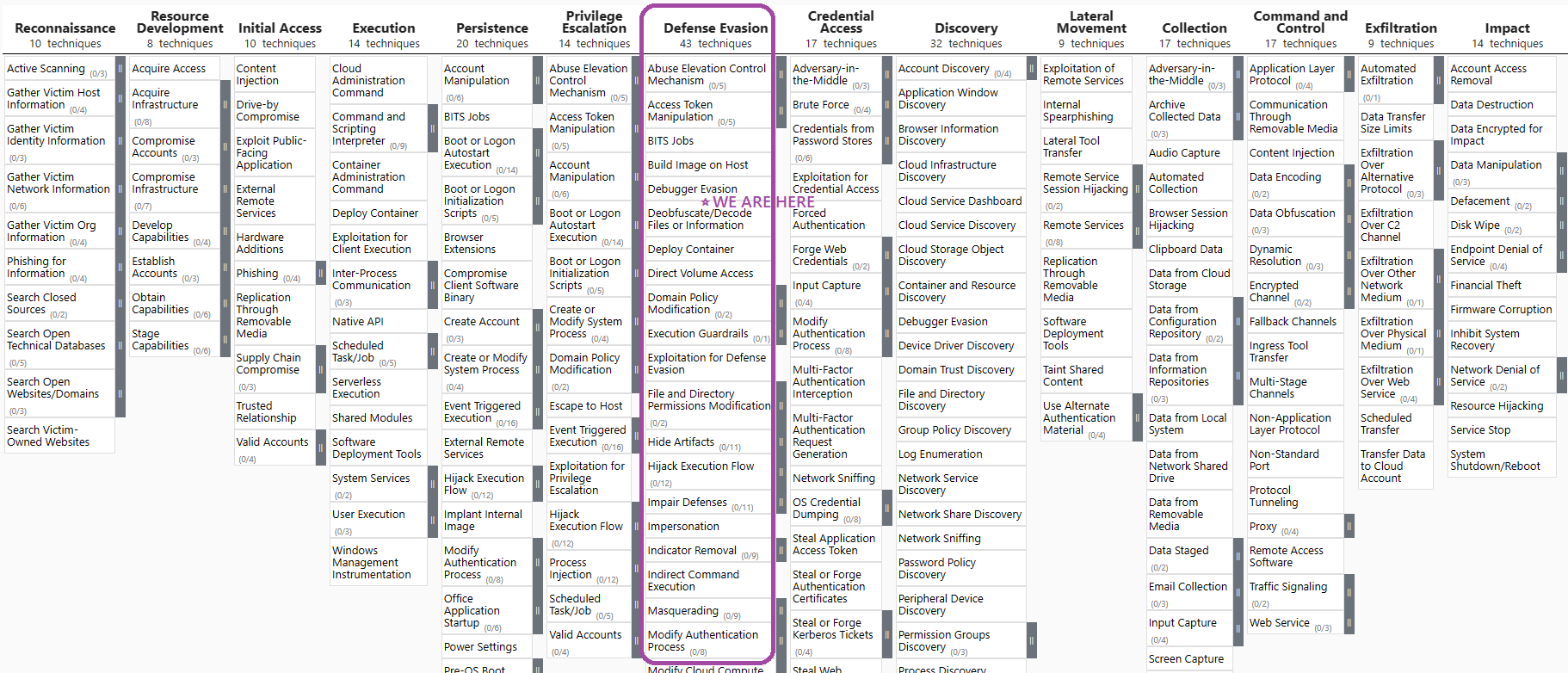
“Defense Evasion” is a tactic used in cyberattacks that involves methods and techniques to avoid detection by security defenses and to obfuscate or hide the presence of malware or malicious activities. The primary goal of defense evasion is to maintain persistence on a system or network without being detected. This allows attackers to carry out their objectives, whether it’s data theft, system exploitation, or creating a backdoor for future access. This blog will explore and categorize specific alerts from Other security alerts documentation.
T1207 Rogue Domain Controller
| External ID | Name | Sev. | Description |
| 2028 | Suspected DCShadow attack (domain controller promotion) | High | Manipulation via Replication: DCShadow is a sophisticated attack where an adversary attempts to manipulate AD data by simulating the behavior of a domain controller. Rogue Domain Controller ①: The attack involves creating a rogue domain controller on the network using the replication process. This is typically done from any machine in the network. Detection in Defender for Identity: Microsoft Defender for Identity can trigger a security alert when it detects a machine in the network trying to register as a rogue domain controller. |
| 2029 | Suspected DCShadow attack (domain controller replication request) | High | Manipulation via Replication: The DCShadow attack involves manipulating Active Directory data by simulating domain controller activities, particularly focusing on the replication process. Active Directory Replication: In a normal setup, AD replication is a process where changes made on one domain controller are synchronized across other domain controllers in the network. Detection in Defender for Identity: Microsoft Defender for Identity generates an alert when a suspicious replication request is made against a genuine domain controller. This is considered a strong indicator of a DCShadow attack. |
① A rogue domain controller is not officially set up or sanctioned by network administrators. It is created by attackers to carry out malicious activities within an AD environment. It can be considered “fake” in the sense that it is not part of the legitimate AD setup. However, it is usually fully functional and capable of performing many of the tasks that a legitimate domain controller would perform. In theory, network administrators should be able to see and identify a rogue domain controller through various administrative tools and logs. However, attackers often use sophisticated techniques to hide their activities.
Other Combined Tactics
| External ID | Name | Sev. | Description |
| 2025 | Suspicious VPN connection | Medium | Behavioral Learning: Microsoft Defender for Identity employs a machine learning algorithm to understand and model each user’s typical VPN usage patterns. This learning is based on factors like which machines users log into and the locations from which they connect. 30 Days Observation: The system requires a minimum of 30 days from the first VPN connection to accurately learn a user’s behavior. Minimum Activity: Additionally, there must be at least 5 VPN connections made by the user in the last 30 days to ensure the model has sufficient data for analysis. |