ATT&CK for Enterprise – TA0007 Discovery
Discovery, Tactic TA0007 – Enterprise | MITRE ATT&CK®
“Discovery” in the context of cybersecurity refers to a tactic used by attackers after they have already gained access to a system or network. The primary objective of Discovery is to gather detailed information about the internal environment of the compromised system, such as system configurations, network resources, user accounts, and services running. This information helps attackers understand the scope and layout of the internal environment, enabling them to plan subsequent stages of their attack, including lateral movement, privilege escalation, or data exfiltration. This blog will explore and categorize specific alerts from Reconnaissance and discovery alerts documentation.
Unlike Reconnaissance, which is about gathering information before an attack, Discovery focuses on exploring and understanding an already compromised system to maximize the effectiveness of further malicious activities.
The main difference between Discovery and Reconnaissance lies in their timing and objectives in the attack lifecycle. Reconnaissance is about gathering information before an attack to inform strategy and target selection, while Discovery is about understanding and exploring a compromised environment to facilitate further malicious activities.
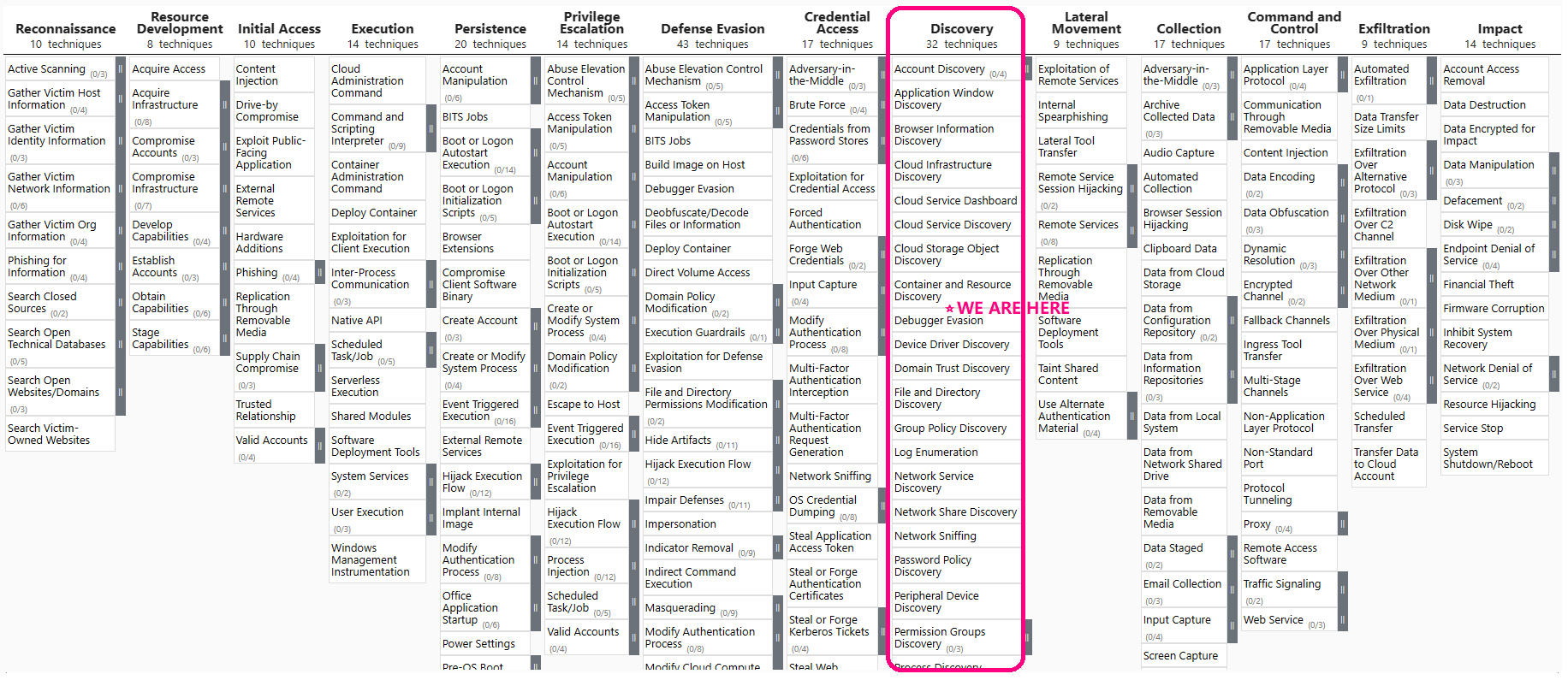
T1087 Account Discovery
| External ID | Name | Sev. | Description |
| 2003 | Account enumeration ② reconnaissance | Medium | Methodology: Attackers use a large list of possible usernames (often sourced from a dictionary) or tools like KrbGuess ① to make educated guesses about usernames in the domain. The process involves systematically attempting to authenticate using these usernames. Kerberos: The attacker makes Kerberos authentication requests with these usernames. A successful guess of a username results in a “Preauthentication required” response from the server, as opposed to a “Security principal unknown” error for invalid usernames. NTLM: The attacker uses the NTLM authentication protocol in a similar manner. A correct username guess yields a “WrongPassword” (0xc000006a) error, whereas an incorrect guess returns a “NoSuchUser” (0xc0000064) error. Detection by Defender for Identity: Microsoft’s Defender for Identity system is designed to detect such account enumeration attacks. It does this by monitoring authentication events from sensors installed on domain controllers and AD FS / AD CS servers. The system tracks where the enumeration attack originates, the total number of guess attempts, and the number of successful matches. If the system observes a high number of attempts with unknown users, it flags this as suspicious activity. |
| 2012 | User and IP address reconnaissance (SMB) | Medium | Nature of the Reconnaissance: The attack specifically targets the enumeration of SMB sessions. Enumeration in this context means collecting information about active SMB sessions on networked computers, particularly domain controllers. By enumerating SMB sessions, attackers can discover where users have recently logged on, which includes obtaining usernames and associated IP addresses. Goals of the Attackers: With the obtained information, attackers can identify active user accounts and their associated machines within the network. This information can be used for lateral movement. Triggering an Alert: The attack triggers an alert when an unusual or unauthorized SMB session enumeration is performed against a domain controller. |
| 2210 | Active Directory attributes reconnaissance (LDAP) | Medium | Methodology: In this attack, threat actors use LDAP to gain information about the AD environment. This could include mapping the domain structure, identifying user accounts, especially those with higher privileges, and understanding the security setup. Defensive Measures: Organizations can mitigate this risk by monitoring and controlling LDAP traffic, implementing strong access controls, regularly auditing AD objects and permissions, and educating staff about recognizing and reporting unusual network activity. |
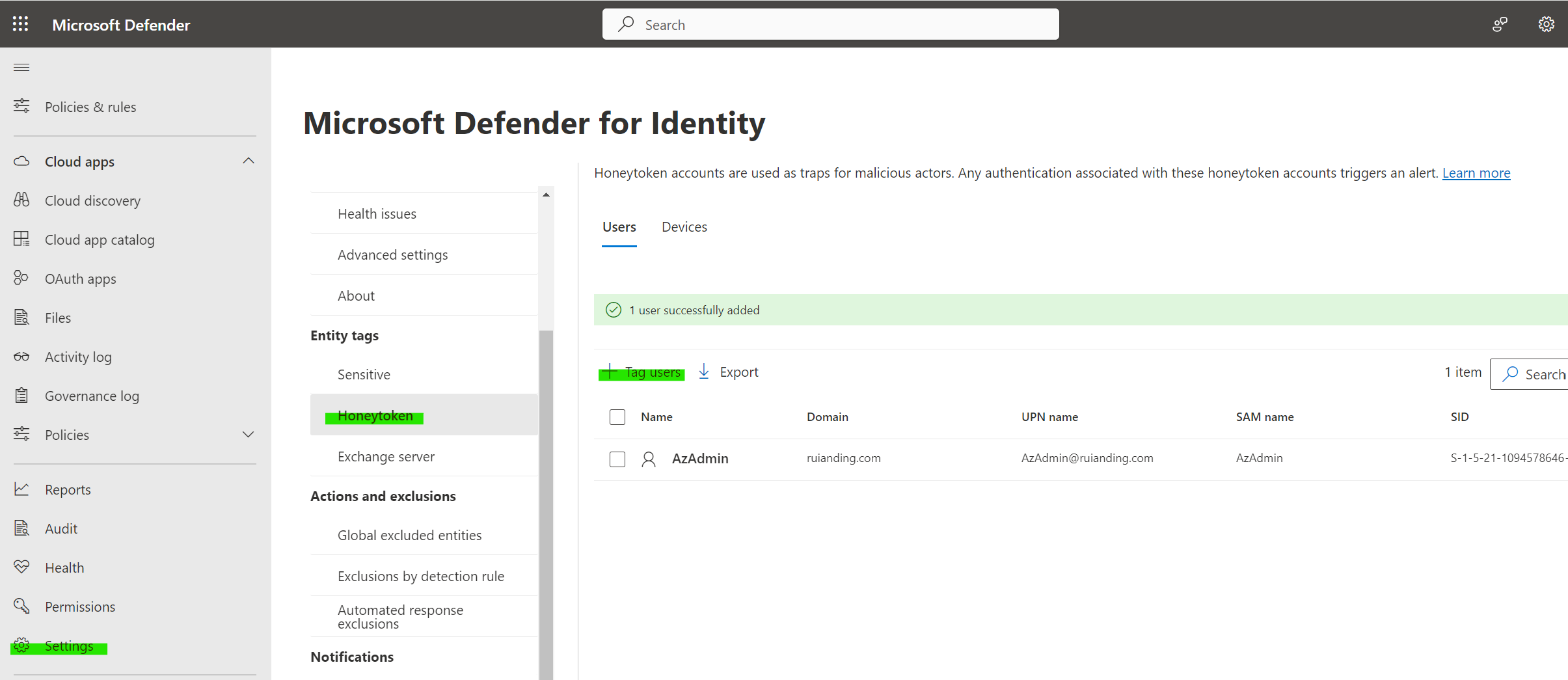
| 2426 | Honeytoken was queried via SAM-R | Low | Attack Context: Attackers use user reconnaissance to understand the directory structure of a network and identify privileged accounts, which can be targeted in later stages of an attack. Detection by Defender for Identity: Microsoft Defender for Identity triggers an alert when it detects SAM-R queries targeting this honeytoken user ③ This is indicative of reconnaissance activity within the network. Severity Assessment: The severity of this attack is rated as low. This is because the querying of a honeytoken itself doesn’t cause direct harm to the network or its operations. However, it’s an indicator of a potential threat actor probing the network. |
| 2429 | Honeytoken was queried via LDAP | Low | Similarly to the previous example, in this case, Microsoft Defender for Identity generates an alert when it detects LDAP queries directed at the honeytoken user. |
① KrbGuess is a tool designed for use in security testing and auditing environments, specifically targeting the Kerberos authentication protocol. The tool sends authentication requests to a Kerberos KDC using different usernames. The KDC typically responds differently to requests involving valid usernames than it does to invalid ones. By analyzing the responses from the KDC, KrbGuess can determine whether a guessed username is likely to be valid within the domain.
② T1087.002 Domain Account Adversaries may attempt to get a listing of domain accounts. This information can help adversaries determine which domain accounts exist to aid in follow-on behavior such as targeting specific accounts which possess particular privileges.
③ A honey token is a digital or virtual bait/decoy designed to mimic a valuable resource in a system, like a user credential, a database entry, or a file. The key idea is that the honey token appears valuable to a potential intruder but is actually monitored and controlled by the system’s defenders. Honey tokens are closely monitored. Any access or interaction with them triggers alerts to the security team, indicating a potential intrusion or malicious activity.
https://learn.microsoft.com/en-us/defender-for-identity/entity-tags
T1046 Network Service Discovery
| External ID | Name | Sev. | Description |
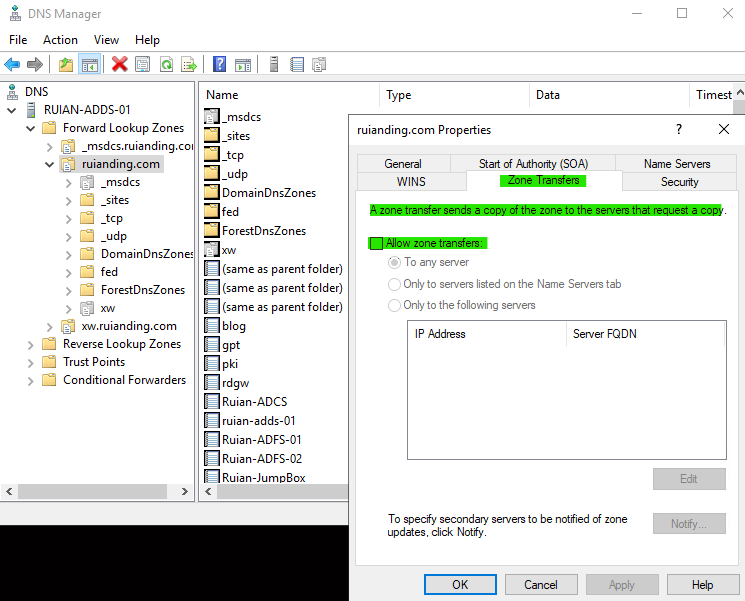
| 2007 | Network-mapping reconnaissance (DNS) | Medium | Target: Attackers target DNS servers to extract this information, which helps them understand the network’s structure, including identifying key servers and devices that can be targeted in later stages of an attack. Method of Reconnaissance: Attackers use specific types of DNS queries to gather this information. One common method is an AXFR (DNS zone transfer) ① request. In a legitimate context, AXFR is used to replicate DNS databases across different DNS servers. However, attackers can abuse this request to gain a complete copy of all DNS data for a domain, which is highly valuable for understanding network topology. Another method involves making an excessive number of DNS queries, which can also reveal important information about the network. Detection by Defender for Identity: Microsoft’s Defender for Identity system detects such reconnaissance activities by identifying suspicious DNS requests. The system particularly looks for AXFR requests originating from non-DNS servers (a major red flag) and patterns of excessive DNS queries. It’s important to note that this alert has a learning period of eight days from the start of domain controller monitoring. During this period, the system learns the normal pattern of DNS requests in the network to better identify anomalies. Purpose and Impact: The aim of this reconnaissance technique is to prepare for more advanced attacks by understanding the network layout, identifying vulnerable points, and planning strategic attacks on specific targets within the network. |
① An AXFR (Authoritative Zone Transfer) DNS zone transfer is a process used in the Domain Name System (DNS) to replicate DNS records from a primary DNS server to secondary DNS servers.
In Windows AD DS environments, AXFR is typically disabled by default, primarily for security reasons. Unrestricted DNS zone transfers can expose critical information about a network’s infrastructure to unauthorized users or attackers. Hence, Microsoft and most other DNS service providers configure their DNS services to block unauthorized zone transfers by default.
T1069 Permission Groups Discovery
| External ID | Name | Sev. | Description |
| 2021 | User and Group membership reconnaissance (SAMR) | High or Medium | Target: Attackers use this reconnaissance technique to understand the directory structure of an organization’s network and to identify privileged accounts that could be targeted in later stages of an attack. Role of the SAMR Protocol: The Security Account Manager Remote (SAMR) ① protocol is used to query directory services. Method of Attack: Attackers use SAMR to enumerate user accounts and group memberships within a domain. This can include identifying users with higher privileges or roles, which are particularly valuable targets for further exploitation. The enumeration can be either broad (listing all users and groups) or targeted (focusing on specific, sensitive accounts). Detection and Learning Period: Microsoft’s Defender for Identity system detects unusual or unauthorized use of SAM-R queries. However, to avoid false positives, there is a learning period of one month after its deployment. During the learning period, Defender for Identity profiles normal SAM-R query patterns from various computers in the network. This helps in establishing a baseline of regular activity against which future queries can be compared to identify suspicious behavior. The learning period is four weeks per domain controller, starting from the first network activity involving SAMR against that specific domain controller. |
① SAM-R (Security Account Manager Remote) is a protocol used in Windows environments to perform various administrative tasks related to user accounts and groups, including querying for user and group membership details.
In the Windows environment, directly using the SAMR protocol for queries is not a common operation, as most standard management tools and command-line utilities do not directly expose operations of the SAMR protocol. However, there are advanced and third-party tools that can be used for this purpose, especially in the fields of network security and penetration testing.
In a standalone Windows system, the SAM database exists in the form of a file, whereas in an AD environment, the functionality equivalent to SAM is implemented by the AD database on the domain controllers. The SAMR protocol is used to access this information, but it does not directly interact with the files themselves.
ATT&CK for Enterprise – Exfiltration – Ruian’s Tech Troubleshooting Toolbox (ruianding.com)
Applying the follow GPO can prevent the SAMR attack: