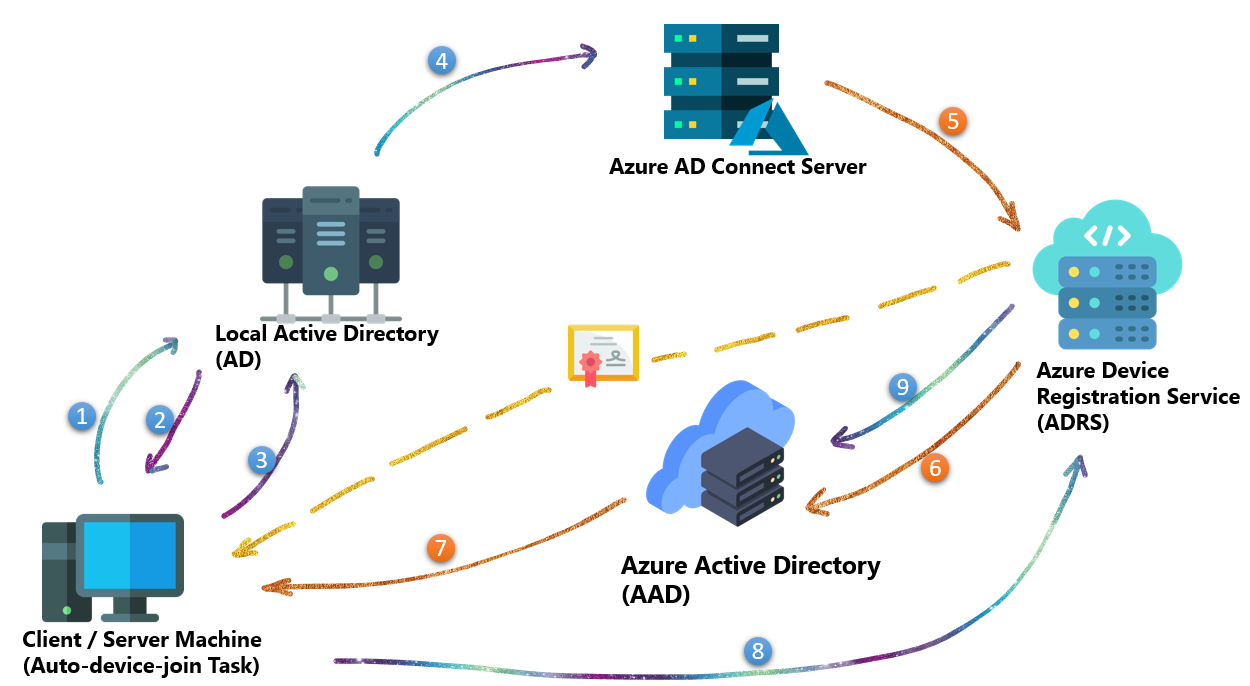
Device Registration Flow – Hybrid Azure AD Join (Managed/Sync Join)
Hybrid Azure AD joined in Managed Environments
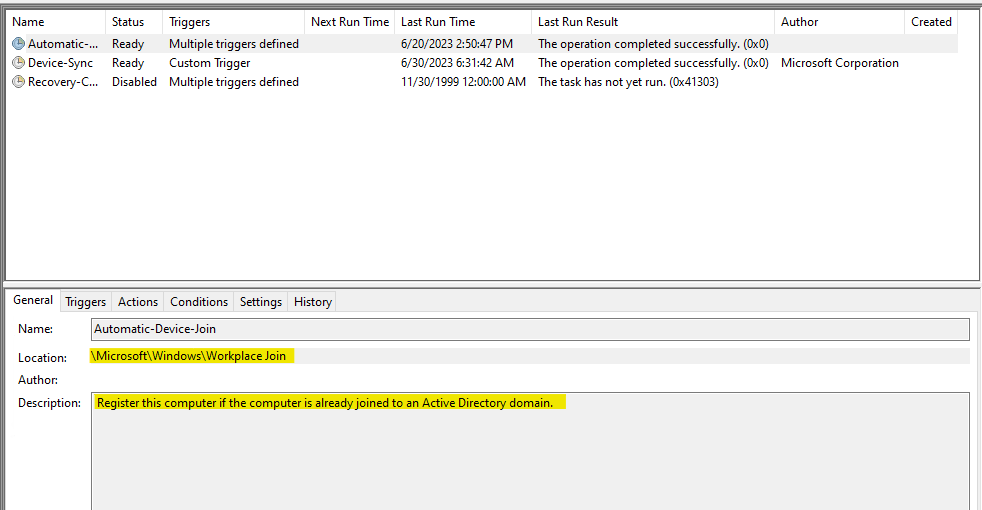
① When user sign-in to a domain joined machine (Windows 10 or newer) using domain credentials. The user sign-in triggers the Automatic-Devic-Join task.
The Automatic-Device-Join task could be found via Task Scheduler > Task Scheduler Library > Microsoft > Windows > Workplace Join > Automatic-Device-Join
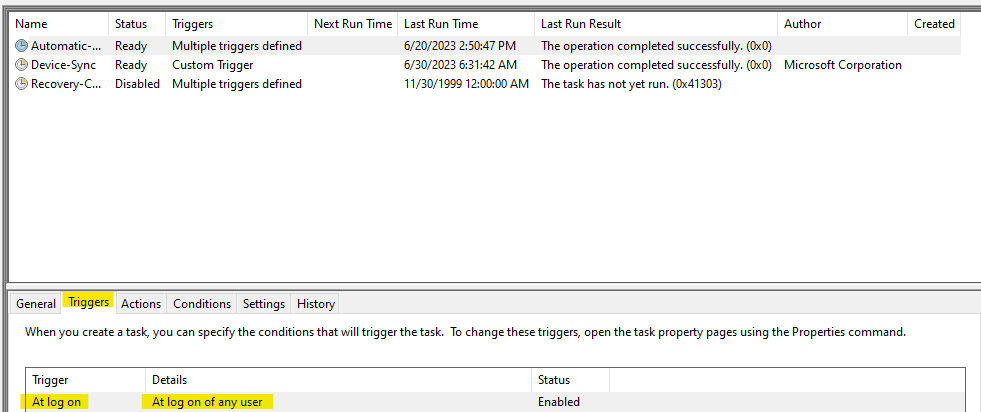
In the Trigger tab we can see by default user sign-in will trigger the task:
The task queries the Service Connection Point (SCP) for registration to discover Azure AD tenant information. SCP may exist in two places: Registry key of the machine & Configuration partition of on-prem AD, which depends on how we configured it.
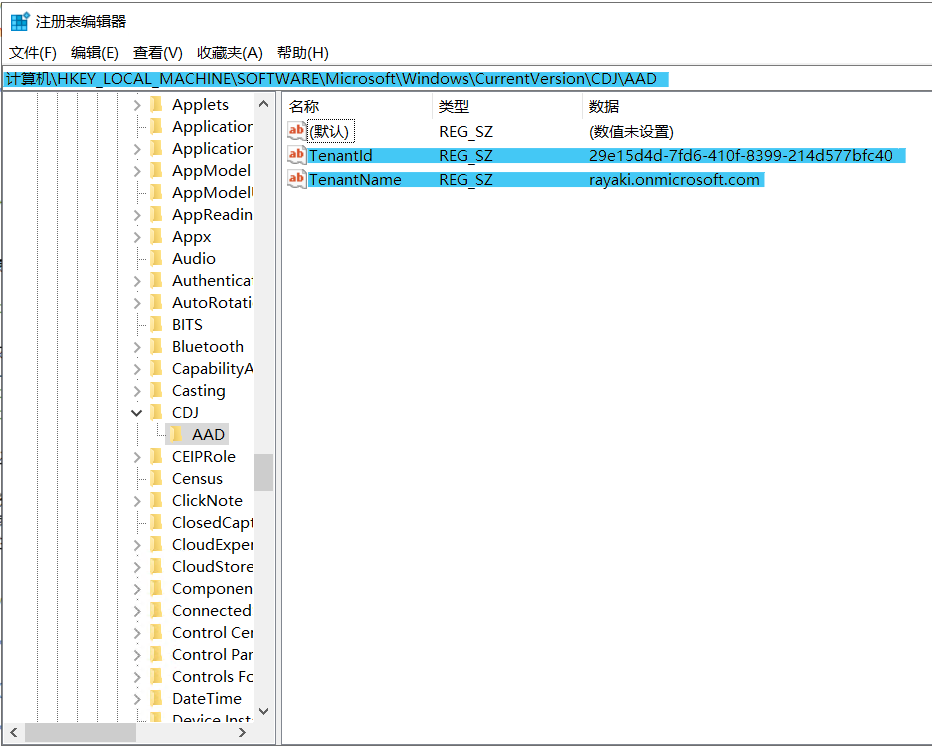
a. In registry key (Used for targeted deployment):
The scheduled task will always have the machine check registry key for SCP value first. The registry key usually configured for targeted HAADJ Targeted deployments of hybrid Azure AD join – Microsoft Entra | Microsoft Learn
Path [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\CDJ\AAD]
b. In the configuration partition in AD (Used for AAD Connect Configuration):
Generally, most administrators would use the AAD Connect to configure the SCP. Therefore, in most cases, we would find the SCP stored in the local AD configuration partition.
② Active Directory using the LDAP protocol for the keywords attribute on the service connection point stored in the configuration partition in Active Directory
CN=62a0ff2e-97b9-4513-943f-0d221bd30080, CN=Device Registration Configuration,CN=Services,CN=Configuration,DC=corp,DC=contoso,DC=com
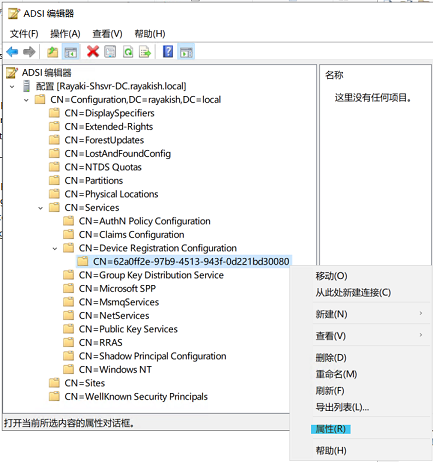
The value specified in the “keywords” attribute determines whether the device registration is directed to Azure Device Registration Service (ADRS) or the on-premises enterprise device registration service.
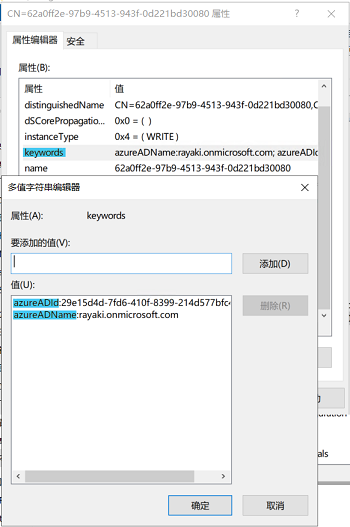
③ In a managed environment, this task generates an initial authentication credential in the form of a self-signed certificate. Subsequently, the task utilizes LDAP to write the certificate to the userCertificate attribute on the computer object in Active Directory.
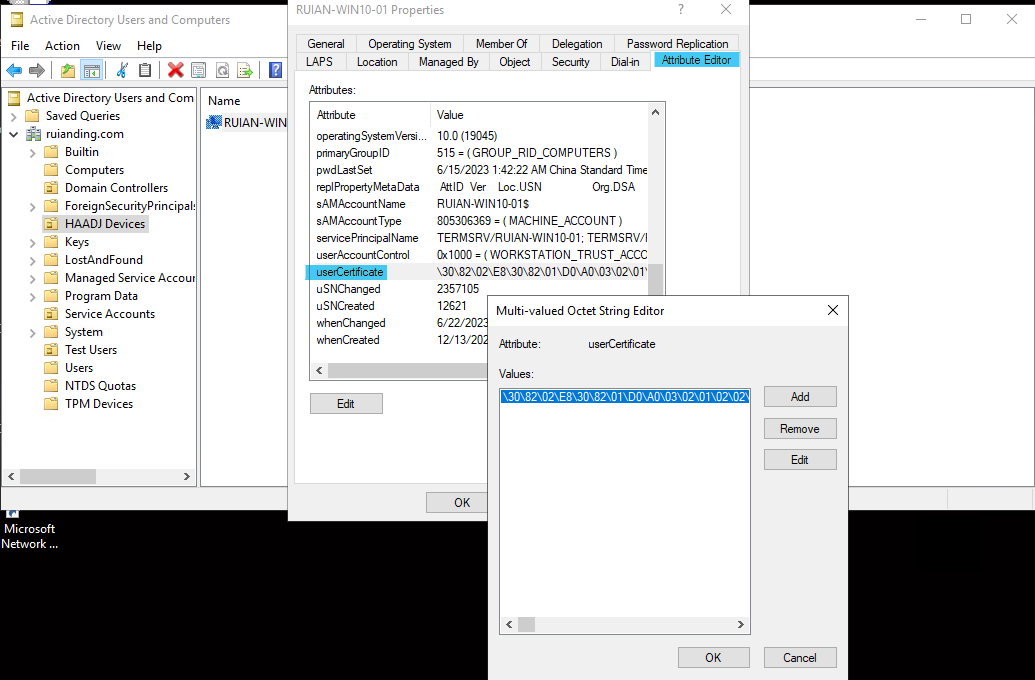
* userCertificate is the public key of the self-signed certificate
④ The computer cannot authenticate with Azure DRS until a device object is created in Azure AD, which includes the certificate in the userCertificate attribute.
⑤ Azure AD Connect detects any changes in attributes. During the next synchronization cycle, Azure AD Connect transmits the userCertificate, object GUID, and computer SID to Azure DRS.
⑥ Azure DRS utilizes userCertificate information to generate a device object in Azure AD. There will be a cloudUserCertificate attribute created. This usually indicates the cloud sync process happens successfully.
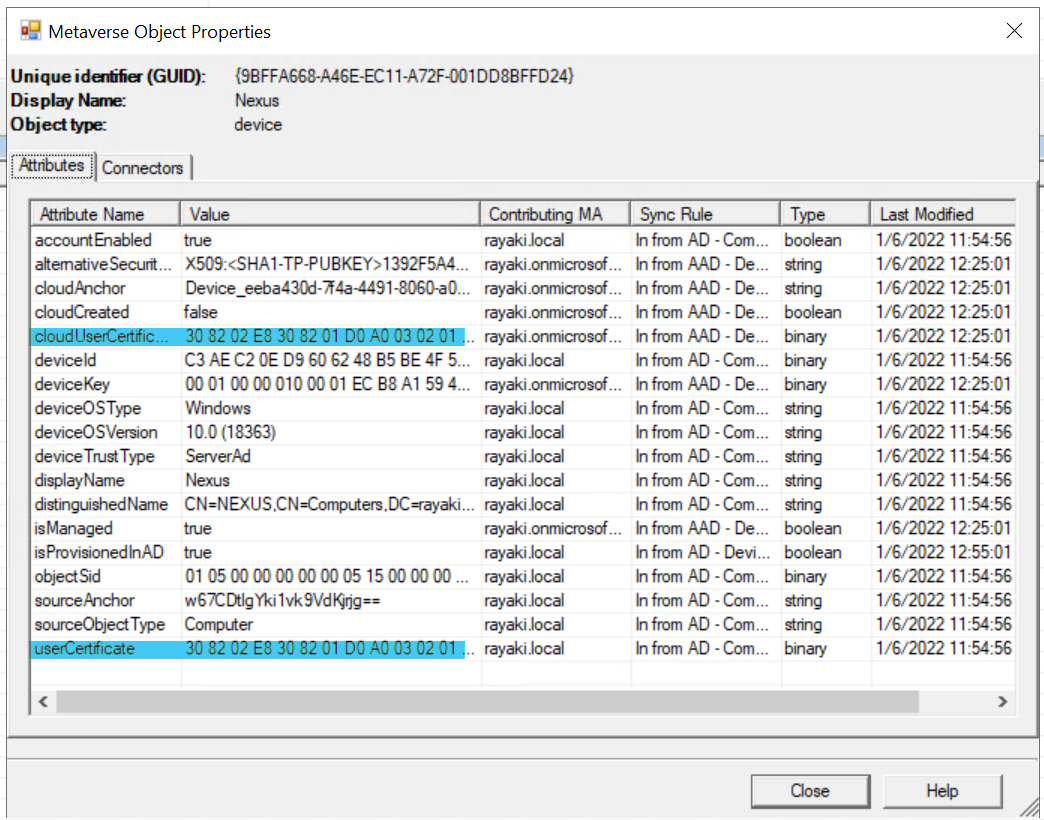
⑦ The Automatic Device Join task is triggered either with each user sign-in or every hour. It attempts to authenticate the computer to Azure AD by utilizing the corresponding private key associated with the public key stored in the userCertificate attribute (we did mention this before). Once authenticated, Azure AD issues an ID token to the computer.
⑧ The task creates TPM bound (preferred) RSA 2048 bit key-pair known as the device key (dkpub/dkpriv). The application creates a certificate request using dkpub and the public key and signs the certificate request with using dkpriv. Next, the application derives second key pair from the TPM’s storage root key. This key is the transport key (tkpub/tkpriv).
The task sends a device registration request to Azure DRS that includes the ID token, certificate request, tkpub, and attestation data.
⑨ Azure DRS validates the ID token, creates a device ID, and creates a certificate based on the included certificate request. Update the device info in AAD.
Later, Azure DRS updates the device object in Azure AD and sends the device ID along with the device certificate to the client.
Subsequently, the device registration process concludes as the client receives the device ID and the device certificate from Azure DRS. The device ID is stored for future reference, accessible through dsregcmd /status command.
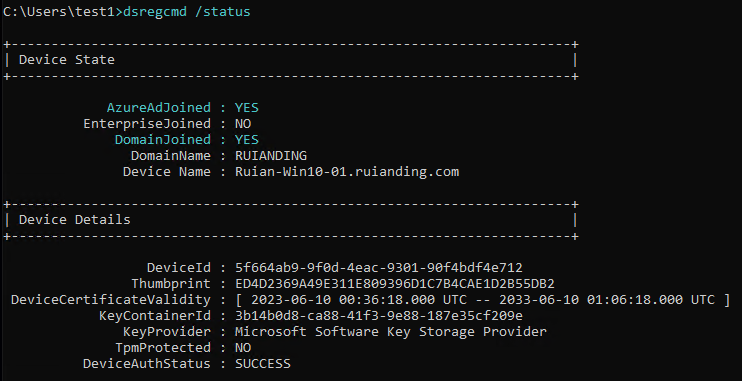
While the device certificate is installed in the computer’s personal store. With the device registration completed successfully, the task concludes and exits.
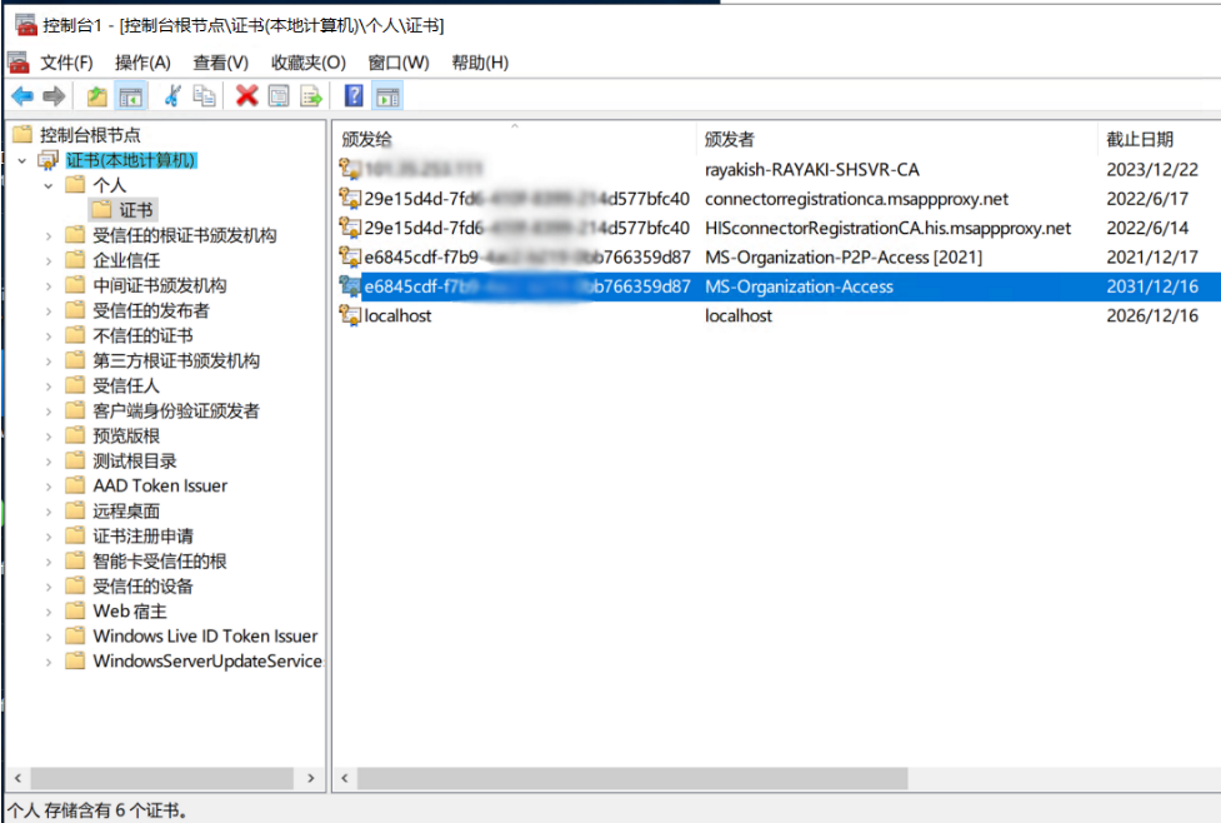
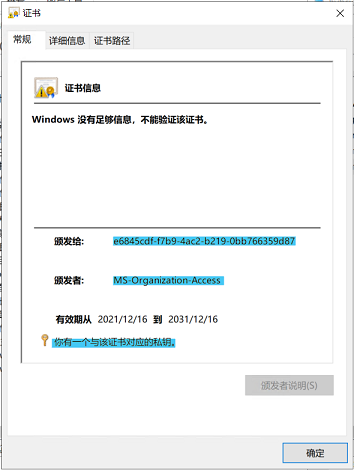
Referencing Microsoft Doc: How Azure AD device registration works – Microsoft Entra | Microsoft Learn
Extra Useful Post: Hybrid Azure AD Device Registration – AzureEra