Execute Processes Remotely with PsExec Tool
Overview
Utilizing the PsExec tool is an efficient method for executing programs on remote systems under different local accounts such as SYSTEM, SERVICE, NETWORK SERVICE, etc. Its lightweight design makes it a practical alternative to traditional telnet. Some of PsExec’s most powerful applications include launching interactive command prompts on remote systems and enabling tools like IpConfig to display information about remote systems.
1. How to Get the PsTools Suite
To download the PsTools package, visit the PsTools – Sysinternals | Microsoft Learn.
Unzip the file and place it in your desired directory.
Open a Command Prompt window with administrative privileges. Navigate to the PsTool folder.
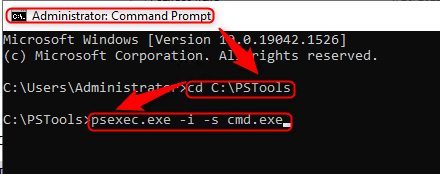
You can now execute remote programs using the psexec.exe command. For instance, to open a new Command Prompt window as the System Account, use the following command:
psexec.exe -i -s cmd.exe
The -i flag allows the program to interact with the remote system’s desktop.
The -s flag enables running the process in the System account.
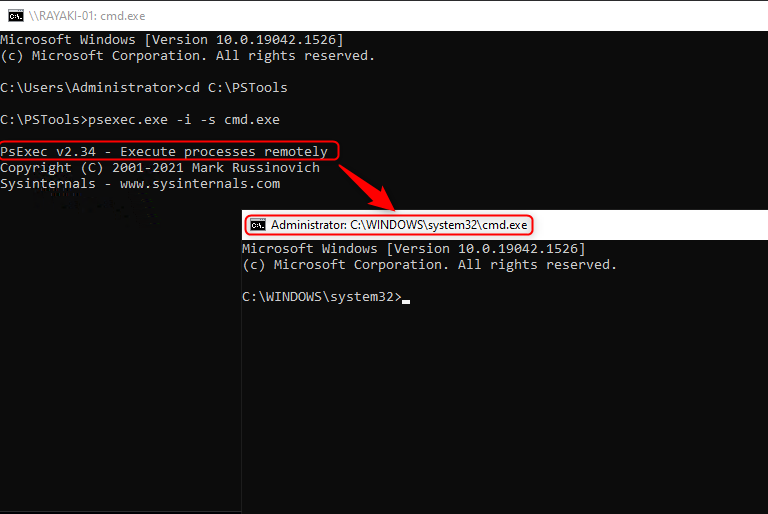
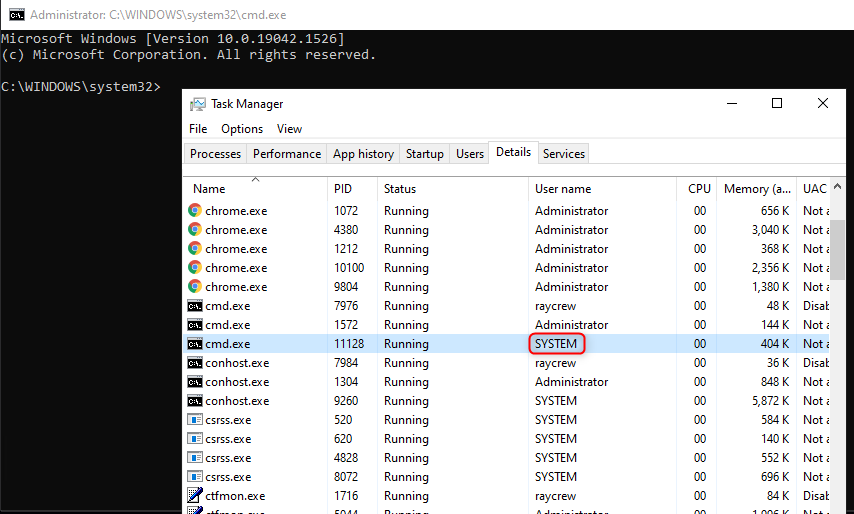
Upon checking the Task Manager, you’ll notice the new Command Prompt window running as SYSTEM.
2. General Implementations of PsExec Tool
?2.1 Checking Microsoft DRS Endpoints Connectivity Under System Account
During the Device Registration process, the device communicates with Microsoft Endpoints under System Context. PsExec can be used to check the connectivity of these endpoints, particularly the enterpriseregistration.windows.net endpoint.
https://enterpriseregistration.windows.net https://login.microsoftonline.com https://device.login.microsoftonline.com
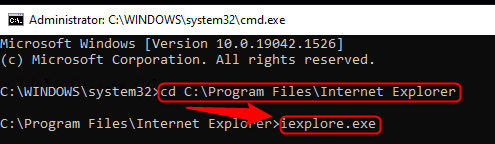
Implement the steps from Section 2 and use the System Account Command Prompt to open a browser (preferably Edge, as Internet Explorer is no longer supported in Windows 11). Third-party browsers like Google Chrome or Mozilla Firefox are also suitable.
Navigate to the browser’s folder, run iexplore.exe, and attempt to access the following DRS discovery URLs:
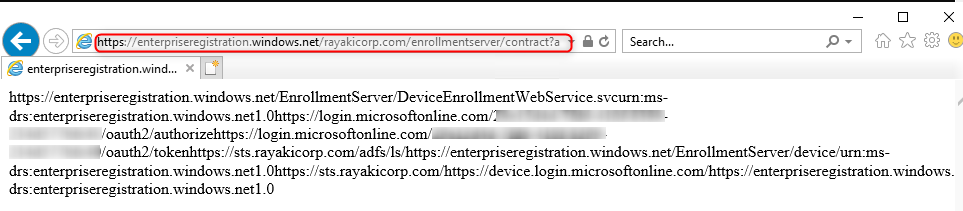
https://enterpriseregistration.windows.net/<VerifiedDomain>/enrollmentserver/contract?api-version=1.2
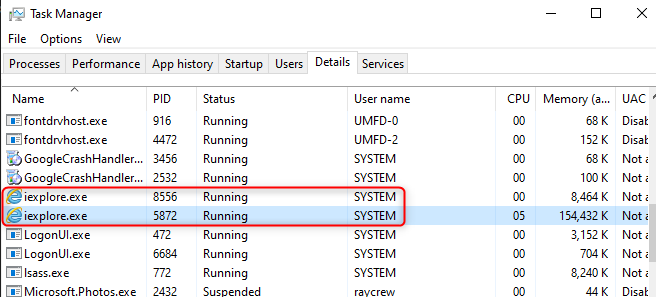
Replace <VerifiedDomain> with your verified Domain Name.
A successful response indicates proper functioning:
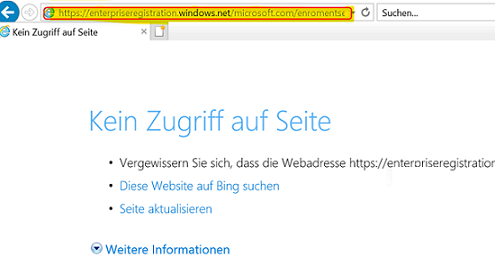
If unsuccessful, consult the Network/Proxy team for potential Winhttp Proxy settings issues:
?2.2 Inspecting Token Signing & Encryption Certificates via ADFS Service Account
The Token Signing and Encryption Certificates are stored within the ADFS Service Account. Use the PsExec tool to access and review these certificates.
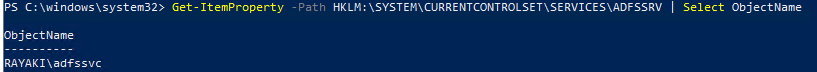
First, confirm the ADFS Service Account using PowerShell:
Get-ItemProperty -Path HKLM:\SYSTEM\CURRENTCONTROLSET\SERVICES\ADFSSRV | Select ObjectName
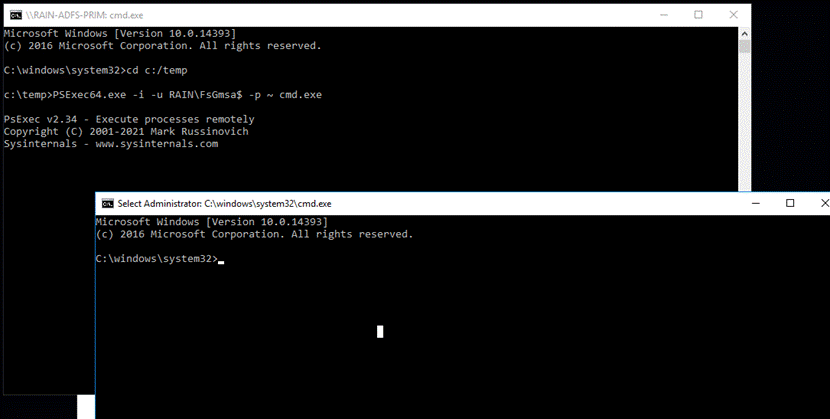
Then, employ the PsExec command to open a new Command Prompt as the ADFS Managed Service Account (FsGmsa$):
psexec.exe -i -u Domain\<ADFS Managed Service Account>; -p ~ cmd.exe
Enter the command to launch the Certificate Management Console and review the stored certificates.
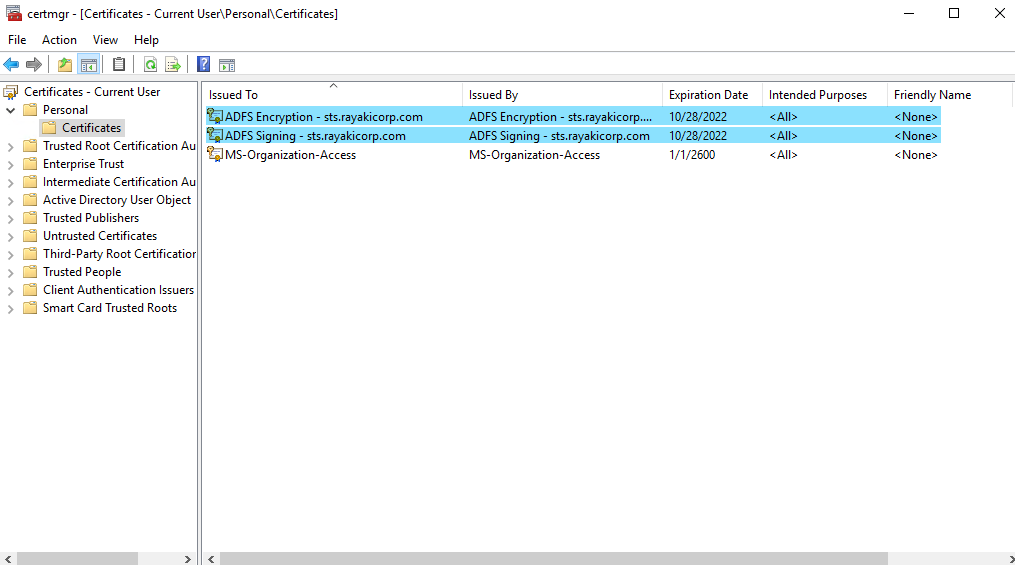
?2.3 Verifying the Certificate Revocation List Under System Account
Since Windows Hello for Business authentication occurs under the system context, you can execute the certutil command to perform a Certificate Revocation List (CRL) check using the system account.
certutil -f –urlfetch -verify mycertificatefile.cer
Basic CRL checking with certutil – Microsoft Community Hub
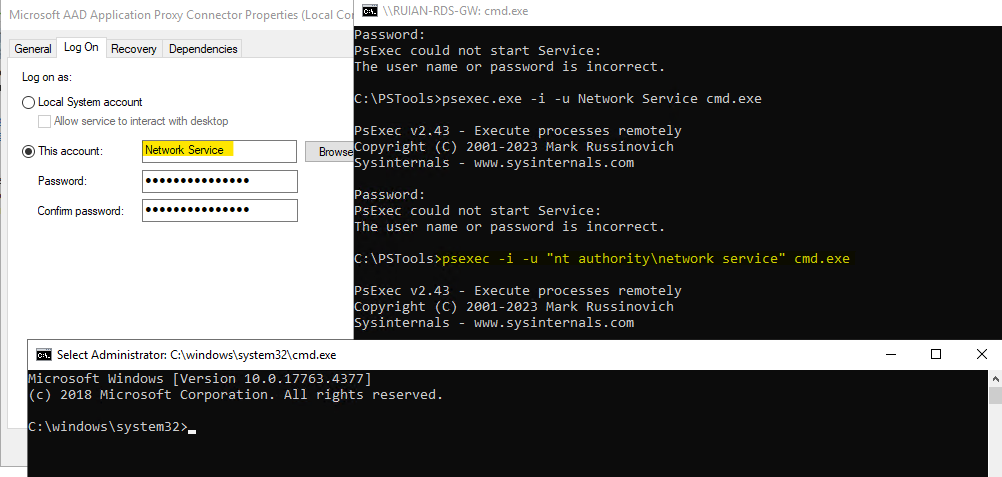
?2.4 Testing Azure AD Application Proxy Connection to On-premises Web App
When using the AADAP connector in environments with a proxy, employ the PsExec tool to remotely access the on-prem application url using the Network Service account. This assists in diagnosing any connectivity issues.
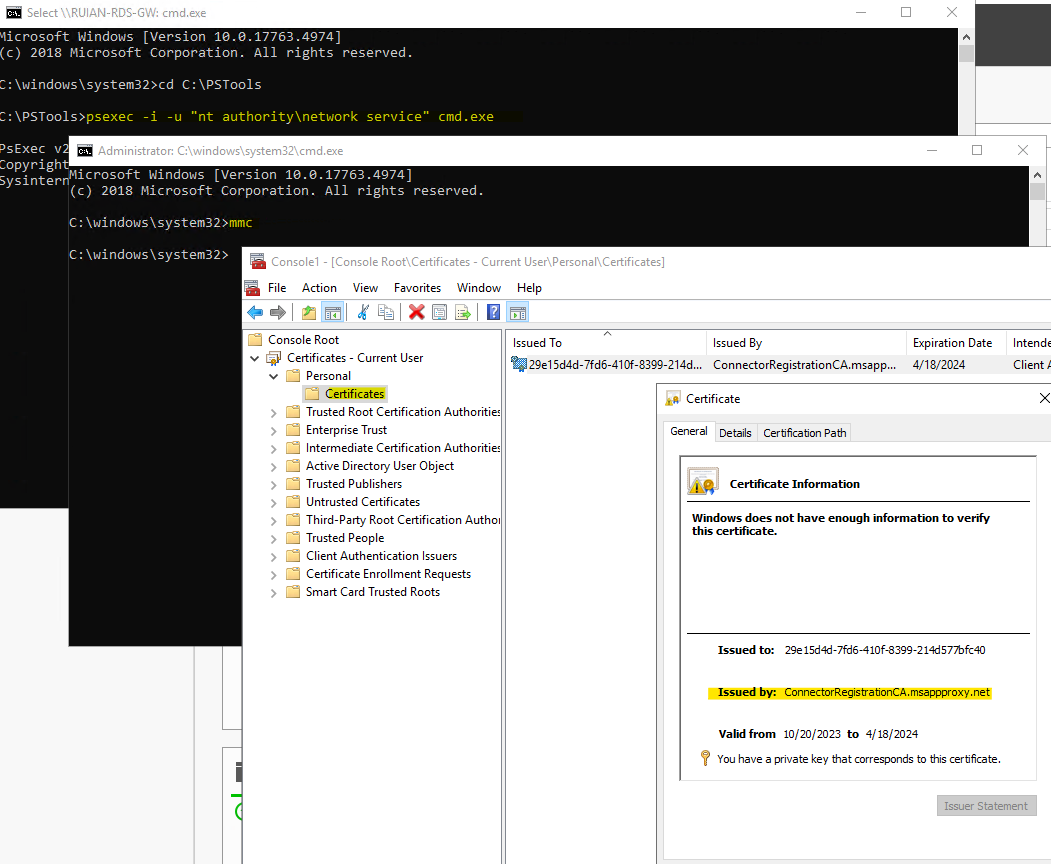
psexec -i -u "nt authority\network service" cmd.exe
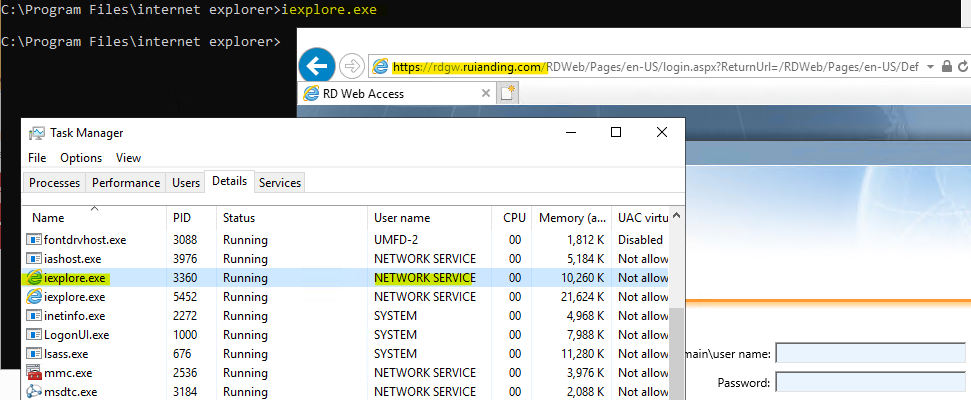
?2.5 Inspecting Connector Registration Certificate via Network Service Account
When we install the AADAP connector or PTA authentication agent, a self-signed certificate is generated to establish trust between the connector server and Azure AD. According to Microsoft documentation, this certificate is set to automatically renew upon expiration.
Initially, the certificate is stored in the local machine’s personal store. However, after renewal, the new certificate is located in the Network Service account’s personal store. The PsExec tool can also be utilized to verify and inspect this certificate.
psexec -i -u "nt authority\network service" cmd.exe