Internet Protocols – Transport Layer Security (TLS)
TLS Concepts
1. What is TLS and Why is it used?
TLS (Transport Layer Security) is a protocol providing secure communication between clients and servers on the internet. TLS operates primarily at the Session Layer (Layer 5) and partially at the Presentation Layer (Layer 6). It ensures data privacy and integrity between two communicating applications.
It’s used for encrypting data transmitted over the internet, like web browsing, email, messaging, and voice-over IP (VoIP).
2. History of TLS and SSL (Secure Sockets Layer)
SSL was the predecessor to TLS, developed by Netscape in the 1990s for securing transactions on the web.
TLS evolved from SSL and was standardized by the IETF. It addressed various security flaws and limitations in SSL.
3. Cryptography in TLS
Symmetric Encryption: Where the same key is used for both encryption and decryption (e.g., AES).
Asymmetric Encryption: Involves public and private keys (e.g., RSA, ECC). Public keys encrypt data that can only be decrypted by the corresponding private key.
Certificates and Keys: Digital certificates (often X.509) are used to verify the ownership of a public key.
TLS Handshake
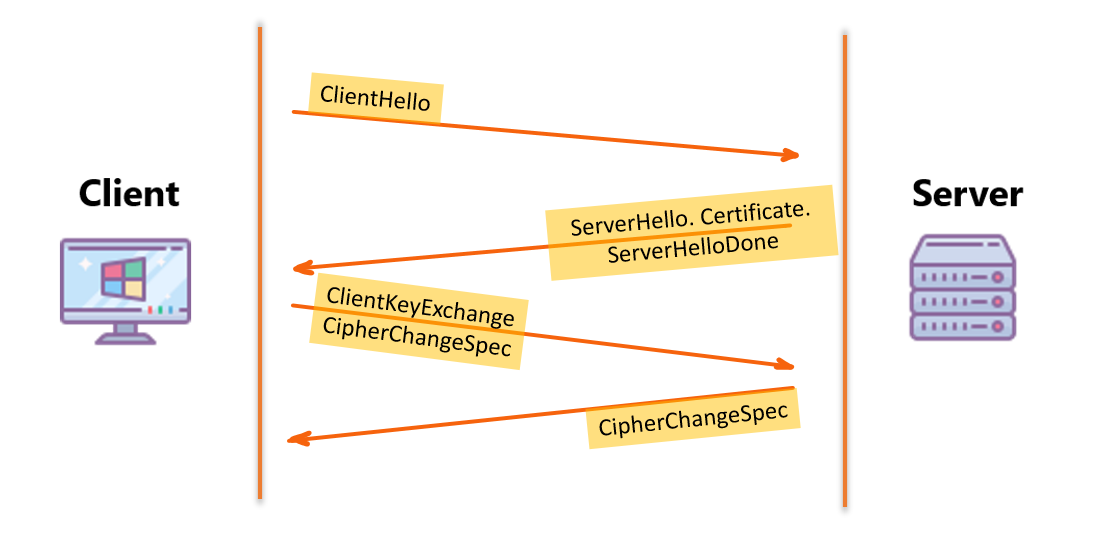
1. Client Hello: The client initiates the handshake by sending a ClientHello message.
This message includes the TLS version the client supports, a list of supported cipher suites (combinations of cryptographic algorithms), a list of supported compression methods, and a random byte string used in later steps.

2.1 Server Hello: The server responds with a ServerHello message.
It chooses the TLS version and cipher suite from the options provided in the ClientHello. The server also generates its own random byte string.
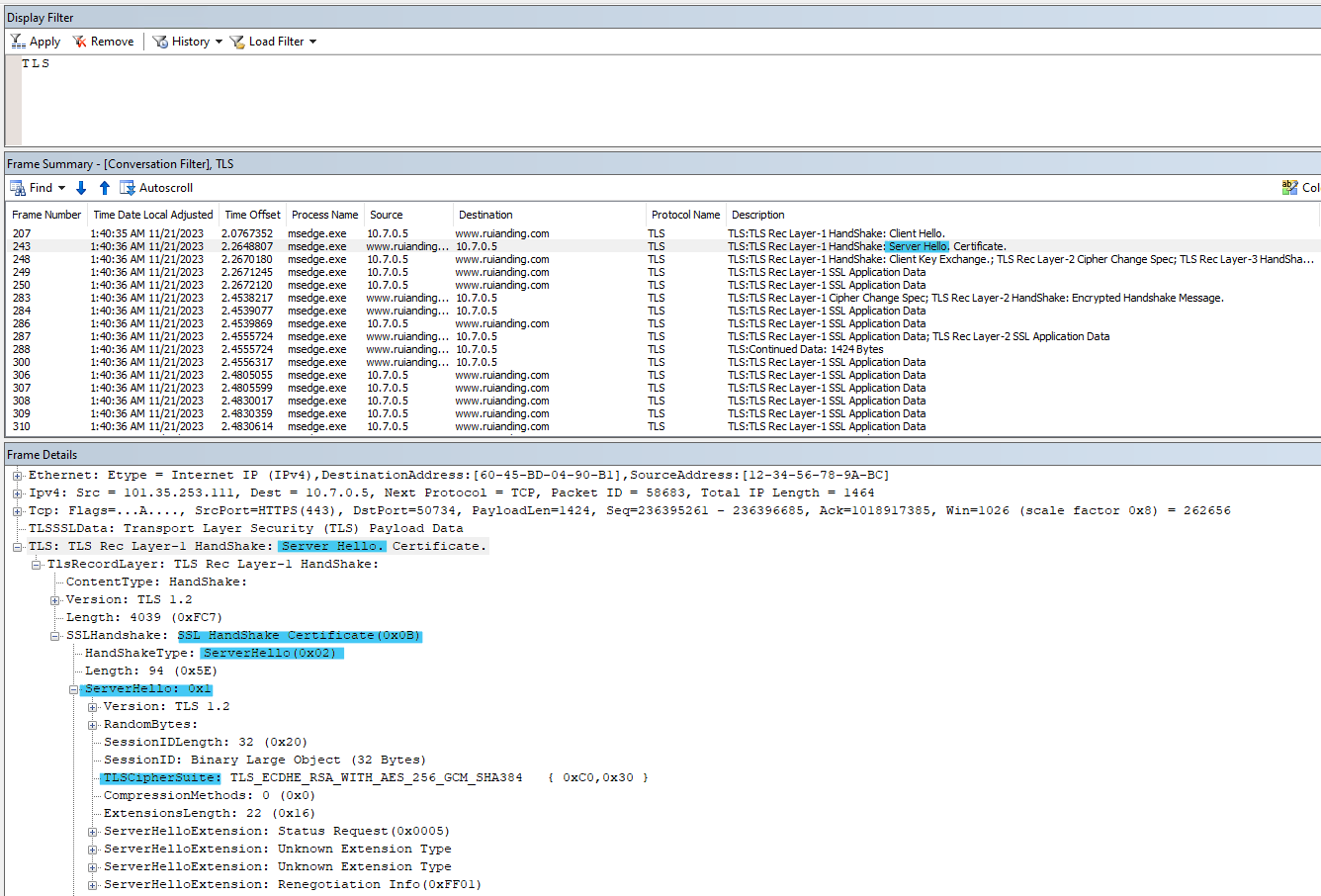
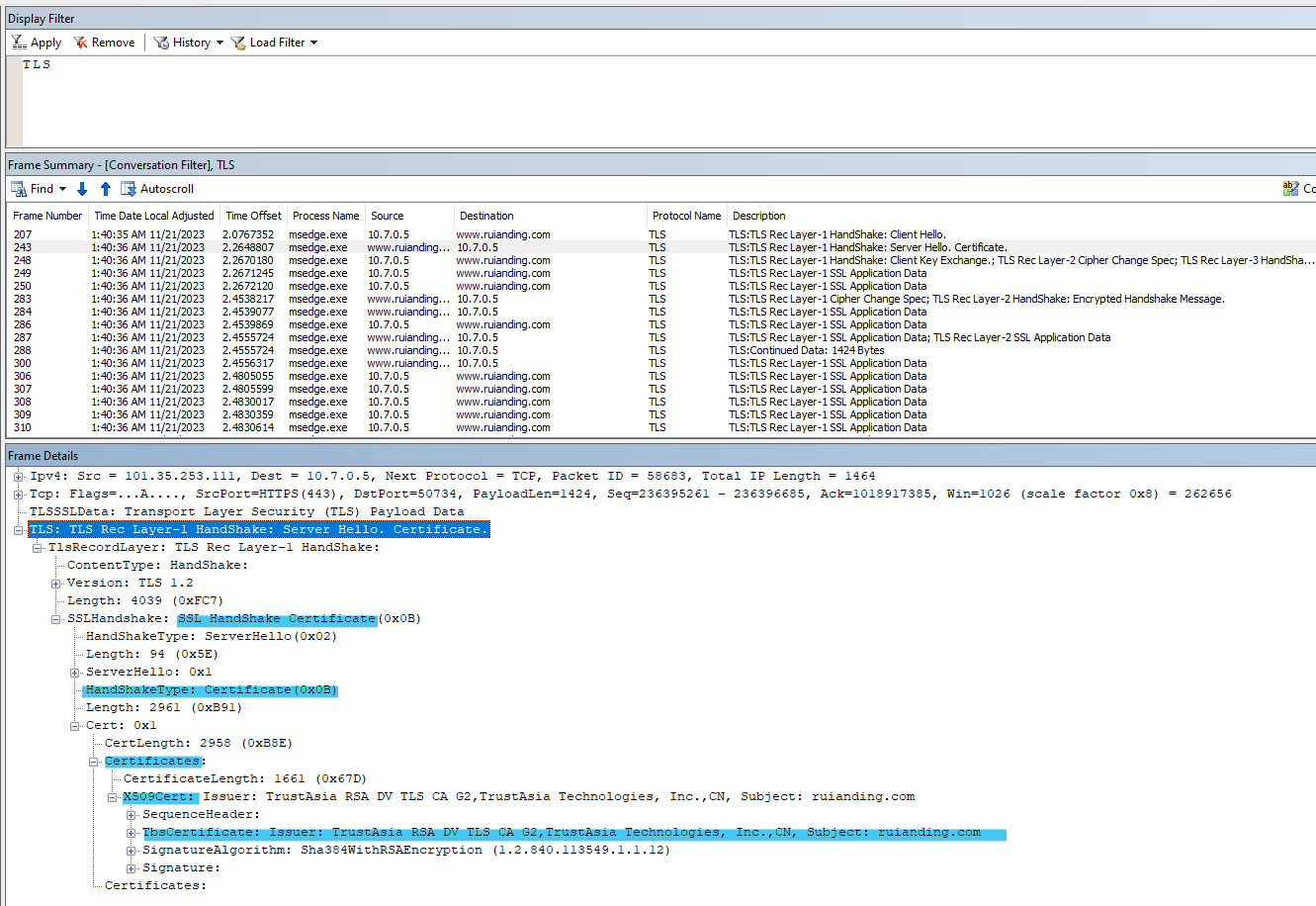
2.2 Certificate: The server sends its digital certificate to the client in a Certificate message.
The certificate usually includes the server’s public key and is issued by a trusted Certificate Authority (CA).
2.3 Server Hello Done: The server sends a ServerHelloDone message, indicating it has finished sending its part of the negotiation.
3. Client Key Exchange: The client sends a ClientKeyExchange message.
It usually contains the pre-master secret encrypted with the server’s public key.
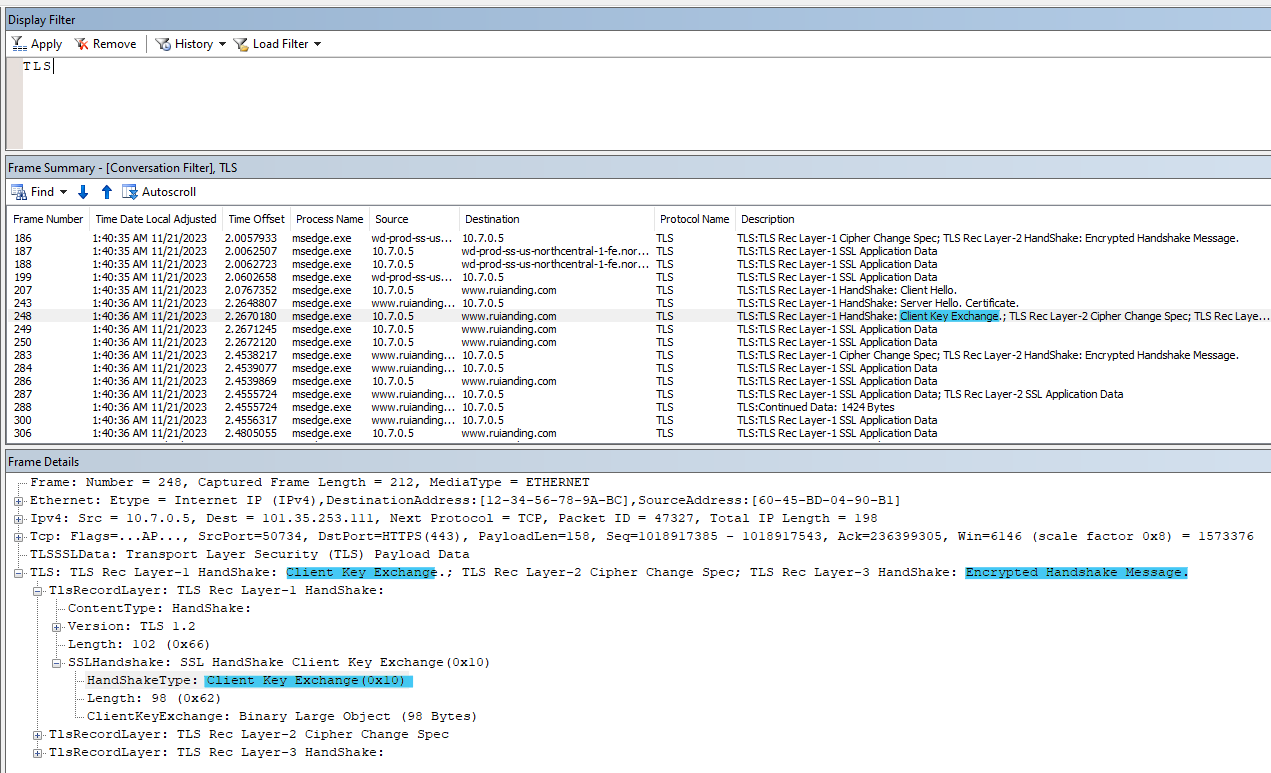
4. Cipher Change Spec: Both client and server send a CipherChangeSpec message, signaling that subsequent messages will be encrypted using the keys derived from the pre-master secret.
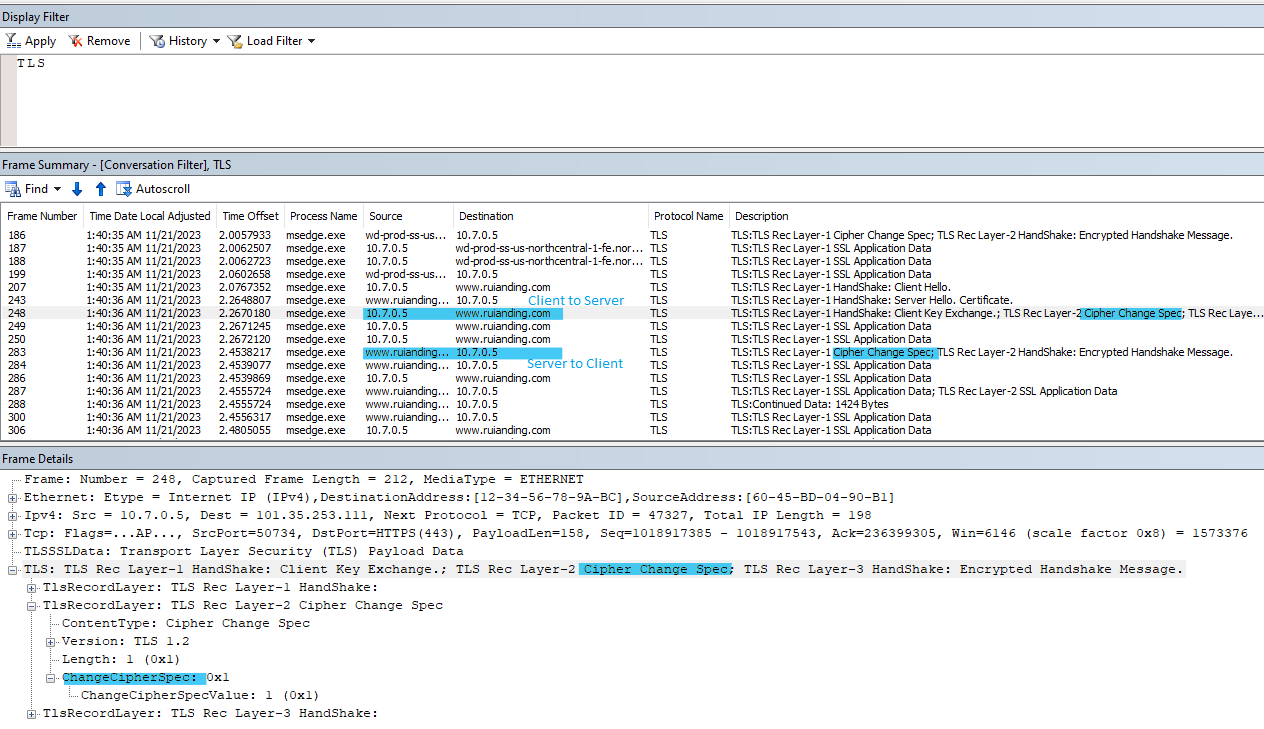
5. Finished: Finally, both client and server exchange Finished messages, verifying that the key exchange and authentication processes were successful.