Turn off the NLA via Registry Key
Enable Remote Desktop on your PC | Microsoft Learn
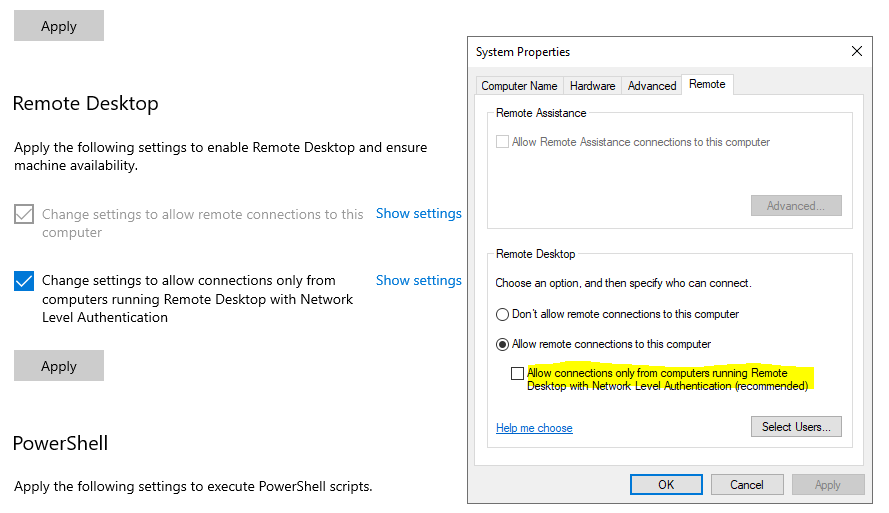
Why allow connections only with Network Level Authentication?
If you want to restrict who can access your PC, choose to allow access only with Network Level Authentication (NLA). When you enable this option, users have to authenticate themselves to the network before they can connect to your PC. Allowing connections only from computers running Remote Desktop with NLA is a more secure authentication method that can help protect your computer from malicious users and software.
If you’re remotely connecting to a PC on your home network from outside of that network, don’t select this option.
In certain scenarios, it may be necessary to disable Network Level Authentication (NLA) if the client does not support it. Sometimes, even after disabling NLA through settings, we may still encounter situations where the non-NLA sign-in experience is not available.
The following registry key path can be a contributing factor that causes NLA to remain enabled. You can use the following commands to check the status:
Reg query "HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp" /v SecurityLayer Reg query "HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp" /v UserAuthentication Reg query "HKLM\SOFTWARE\Policies\Microsoft\Windows NT\Terminal Services" /v SecurityLayer Reg query "HKLM\SOFTWARE\Policies\Microsoft\Windows NT\Terminal Services" /v UserAuthentication
Ensure that all the values returned by these commands are set to 0, indicating that NLA is turned off.
By verifying and setting the appropriate values, you can ensure that NLA is disabled and achieve the desired non-NLA sign-in experience.