Windows Local Administrator Password Solution (LAPS) Azure AD Backup
A recent addition to Azure Active Directory is the LAPS feature, originally a Windows feature. LAPS now offers the convenience of automatically managing and backing up local admin account credentials to AAD. Additionally, administrators have the option to back up local administrator credentials on AAD.
1. Feature Prerequisites
1.1 OS Version
- Windows 11 22H2 – April 11 2023 Update
- Windows 11 21H2 – April 11 2023 Update
- Windows 10 – April 11 2023 Update
- Windows Server 2022 – April 11 2023 Update
- Windows Server 2019 – April 11 2023 Update
For a full list of supported OS versions, refer to the MS doc: Windows LAPS overview | Microsoft Learn
1.2 Licensing
- A Windows license is required.
- No AAD license is needed.
- An Intune license is necessary if customers want to utilize Mobile Device Management (MDM).
1.3 Device Registration Type
- Supported join types include Hybrid Azure AD Join (HAADJ) and Azure AD Join (AADJ).
- AAD register is not supported.
2. Configuration
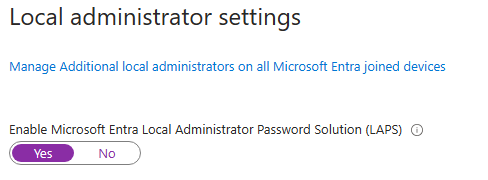
To enable this feature in AAD, navigate to device settings and enable the option for backup to AAD, along with other LAPS settings:
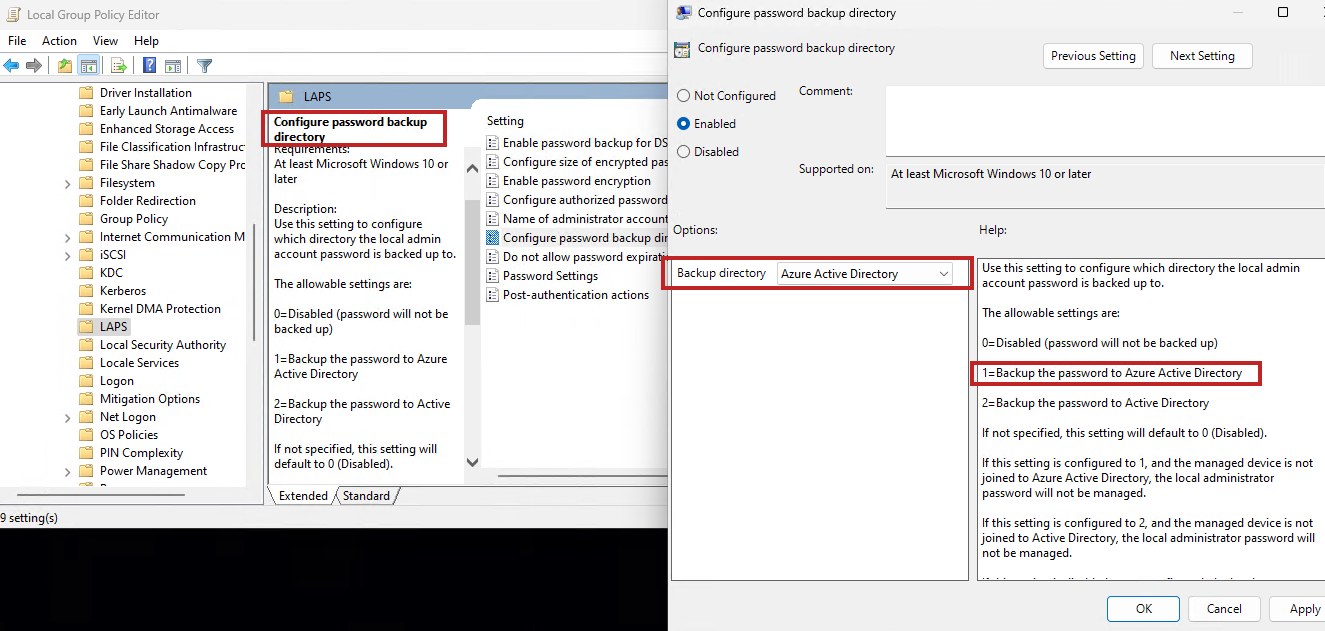
For Group Policy:
Configure password backup directory at Computer Configuration > Administrative Templates > System > LAPS
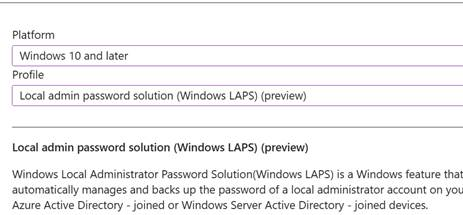
For Intune:
In the Intune Admin portal, go to Endpoint Security > Account Protection and create the policy as specified.
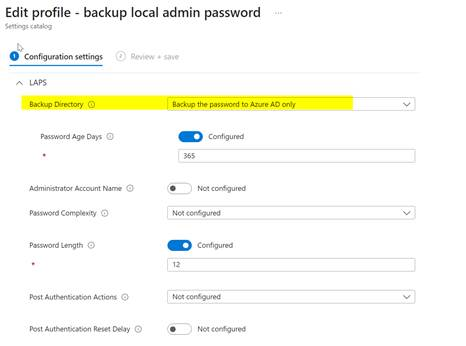
Settings configured via Intune can be found on the device in HKLM\Software\Microsoft\Policies\LAPS.
Administrators can choose to back up the local admin password to AAD or on-premise AD using the respective switch (1 or 2). Some settings are exclusively available when opting for on-premise AD as the backup directory.
3. Monitoring
The LAPS service runs on the device every hour to check for policies. If the backup directory is AAD, it verifies whether the current password has expired according to policy settings. If it has expired, a new password is generated and set, and it is stored in AAD.
In AAD, Global Administrators, Cloud Device Administrators, or Intune Service Administrators are granted permission to access the saved passwords.
To view the clear text password, navigate to Azure Active Directory > Devices > Local Administrator Password Recovery > Show Local Administrator Password.
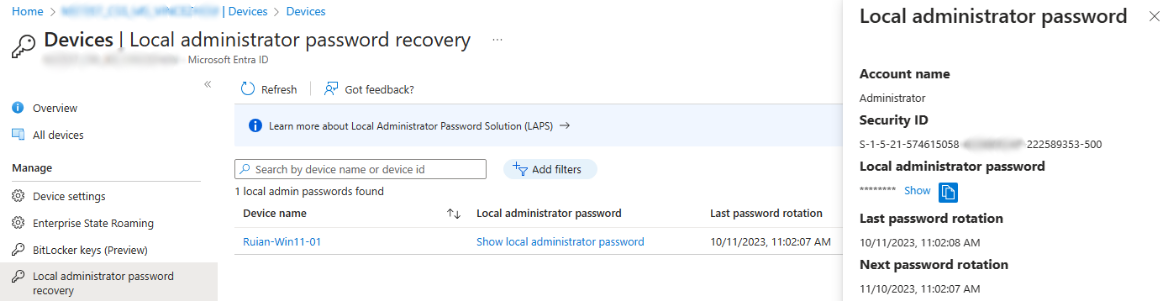
For those interested in programmatic access, the Graph API is available. You can learn more about this in the MS doc: Get deviceLocalCredentialInfo – Microsoft Graph beta | Microsoft Learn
Please note that the password is Base64 encoded in Graph API responses and will need to be decoded before use.